- Security
- Malwarebytes
- 06 March 2016 at 12:35 UTC
-

Malwarebytes Anti-Exploit is a program created by the same company as the famous Malwarebytes Anti-Malware.
This program is very lightweight and very powerful. Moreover, he is unique in its kind because he is designed to block the use of security vulnerabilities (even unknown vulnerabilities : zero-day) present in the various programs that exist.
Malwarebytes has been awarded by several companies specializing in security as : Westcoast Labs, OPSWAT and AV-TEST. And by known sites as : CNET and PC Magazine.



Note : MalwareBytes has created Malwarebytes Anti-Exploit with Zero Vulnerability Labs acquisition.
This anti-exploit is available in 2 versions :
- the free version : Free
- the paid version : Premium
The difference between these these two versions is the number of available shields.
Indeed, the free version currently offers protection against vulnerabilities of these programs :
- web browsers (including : Mozilla Firefox, Google Chrome, Opera and Internet Explorer)
- plugins used by these web browsers (including : Adobe Flash Player, Java, ...)
In addition, the paid version (Premium) also protects you against vulnerabilities of these programs :
- PDF file readers (including : Adobe Acrobat, Adobe Reader and Foxit Reader)
- Office suites (Microsoft Office, OpenOffice and LibreOffice)
- media players (including : VLC, Winamp, QuickTime and Windows Media Player)
- other programs you use, with the ability to add custom shields.
Note : If you are a business, remember that there is also a Business edition : Malwarebytes Anti-Exploit for Business
- Installation
- Register
- Shields enabled in the free version
- Shields enabled in the paid version (Premium)
- Logs
- Exclusions
- Settings
- Advanced settings
- About
1. Installation
To install Malwarebytes Anti-Exploit, simply download and install it.
Then, forget it. It does not need any configuration and will start automatically when Windows starts.
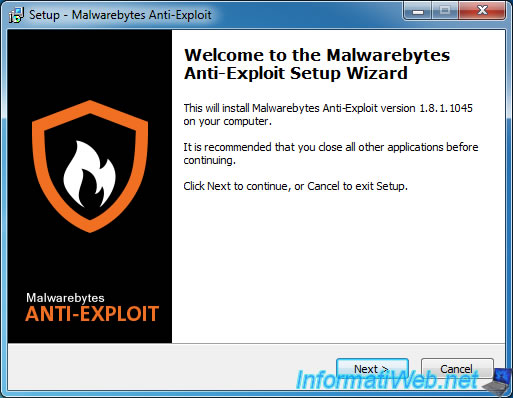
During the installation, Malwarebytes offers a trial of the paid version (Premium) of this program. This will allow you to protect all your programs before you buy it if you want.
That said, you can also use this program in free version if you want. In this case, only web browsers and their plugins will be protected.
Note : most of the time, it's the vulnerabilities of the web browser and/or a plugin of it that are targeted by hackers.
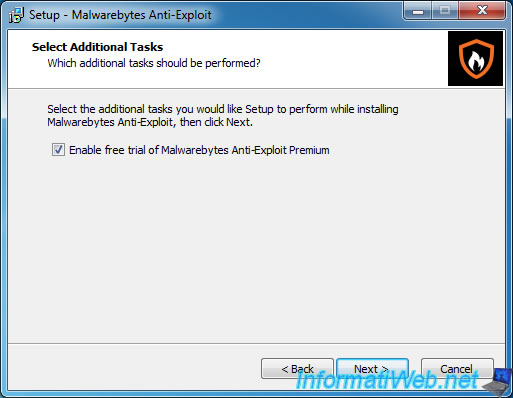

2. Register
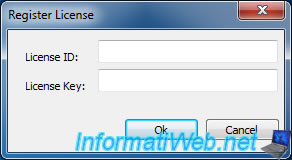
If you bought the paid version (Premium) of Malwarebytes Anti-Exploit, just click on the button "Activate", then type your ID and your serial.
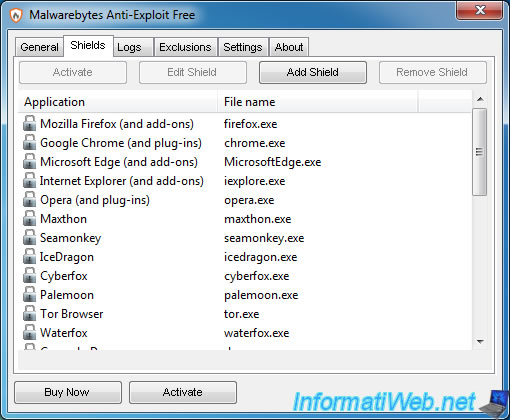
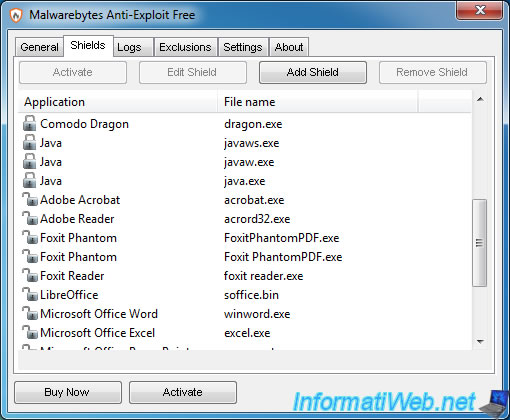
3. Shields enabled in the free version
Currently, the free version protects you against vulnerabilities of these programs :
- known web browsers : Mozilla Firefox, Google Chrome, Microsoft Edge (under Win. 10), Internet Explorer, Opera and their plugins (Flash Player, Java, ...)
- web browsers : Maxthon, Seamonkey, IceDragon (created by Comodo), Cyberfox, ...
- the Java plugin
Note : closed padlocks indicates that these programs are currently protected against vulnerabilities.
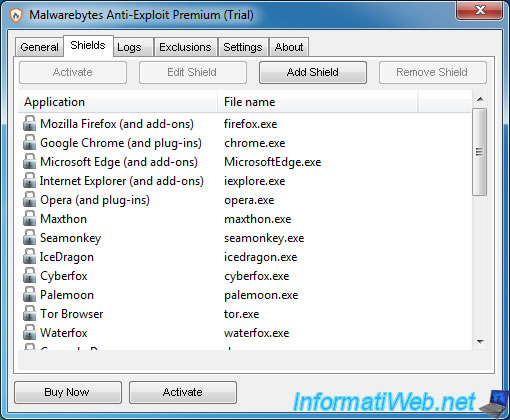
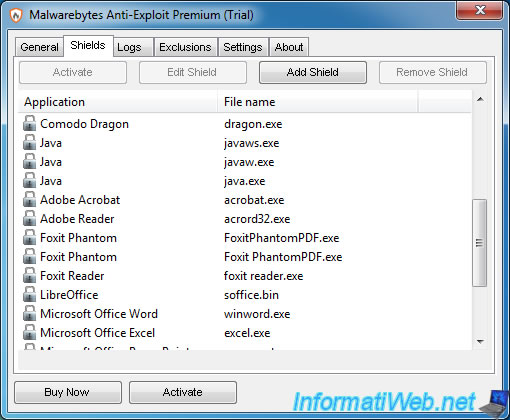
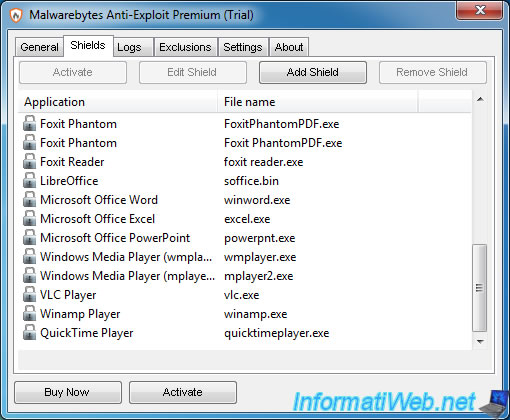
4. Shields enabled in the paid version (Premium)
In the paid version of Malwarebytes Anti-Exploit, you are now protected against these flaws in:
- known web browsers and their plugins (as previously indicated)
- other web browsers like Maxthon, Seamonkey, ...
- the Java plugin
- PDF readers : Adobe Acrobat, Adobe Reader, Foxit Phantom and Foxit Reader
- office suites : Microsoft Office (Word, Excel and PowerPoint) and LibreOffice
- media players : Windows Media Player, VLC, Winamp and QuickTime Player
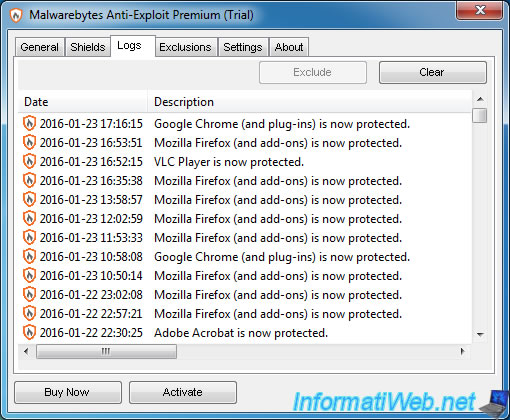
5. Logs
In the "Logs" tab, you will see the history of the activation of shields for each program supported by Malwarebytes.
For each launch of a supported program, a line "[program name] is now protected" is added in this list.
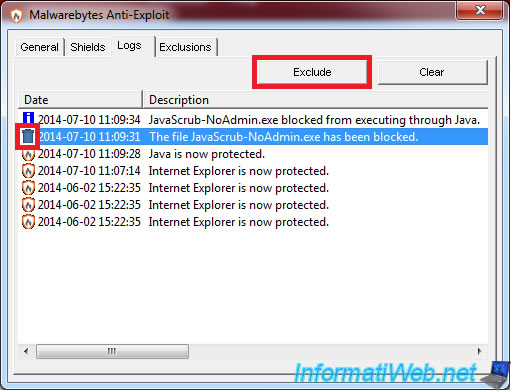
6. Exclusions
If Malwarebytes Anti-Exploit blocks the script of a page that should not been blocked, you can add this detection to exclusions.
To do this, go to the "Logs" tab, select the concerned line (if it has a trash as icon) and click on the "Exclude" button.
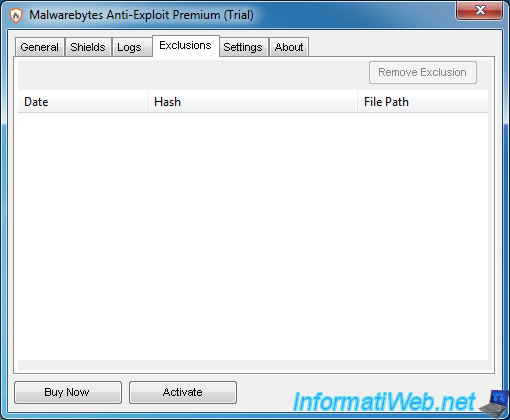
Then, exclusions appear in the "Exclusions" tab.
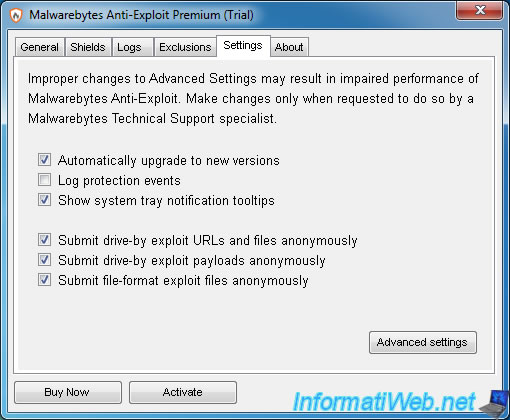
7. Settings
In the "Settings" tab, you can :
- enable or disable the search for new versions of the program. (However, note that this program does not need regular updates)
- log or not the history of protections
- choose whether you want that a tooltip will appear every time Malwarebytes Anti-Exploit protects one of your programs
- choose whether to to help Malwarebytes, by sending samples address (URL), files, ... anonymously.
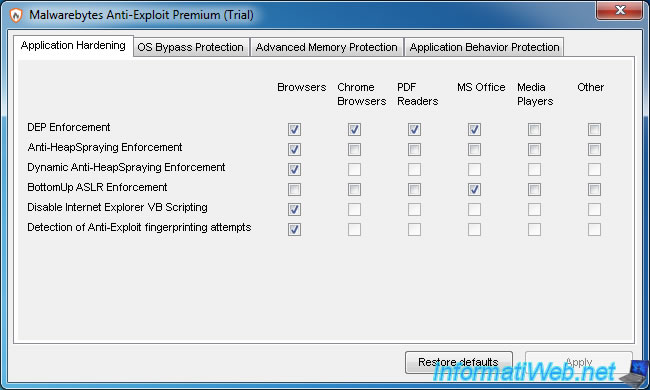
8. Advanced settings
In the advanced settings (this is not recommended to change them), you can enable or disable protections offered by Malwarebytes Anti-Exploit.
For example, one of the first ransomwares was installed on the victim computer by a VB script added to the malicious web page.
As you can see, by default, Malwarebytes Anti-Exploit blocks VB scripts (Disable Internet Explorer VB Scripting) for web browsers (Browser).
The other tabs affect other protection layers provided by Malwarebytes Anti-Exploit.
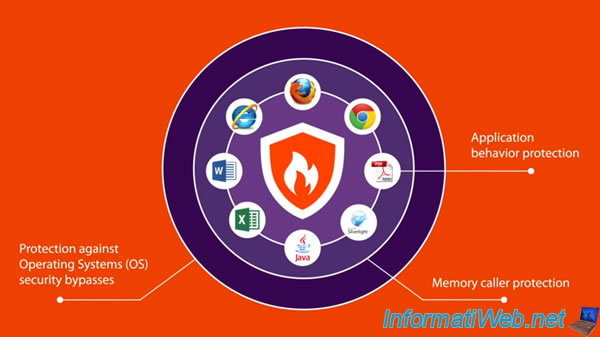
As you can see in the video below, Malwarebytes Anti-Exploit protects you against security holes, with these three layers of security :
- Application behavior protection : Behaviour analysis of the application
- Memory caller protection : protection of memory calls. This prevents that a program edit the memory of another process to which he could not have had access
- Protection against Operating System (OS) security bypasses : protection against the circumvention of security of the operating system, and therefore against the use of vulnerabilities present in it
9. About
In the "About" tab, you will see include:
- the license information
- a link to the program support
- the official website
- Etc.



You must be logged in to post a comment