TrueCrypt - Encrypt your data securely to prevent theft of confidential data
- Security
- TrueCrypt
- 22 May 2014 at 17:57 UTC
-

- 4/4
7. Optional : Install the true or false encrypted container safely
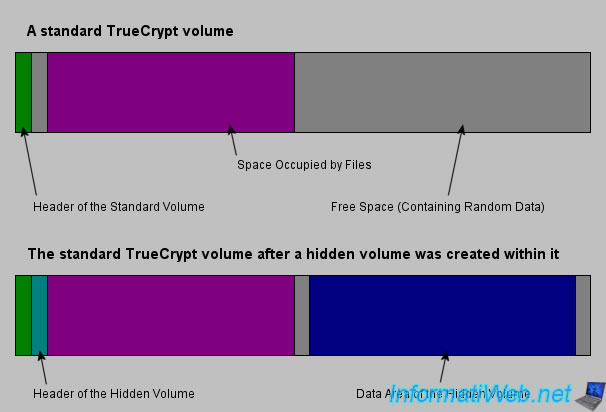
As you may have noticed at the end of formatting the hidden volume, TrueCrypt tells you about to activate a protection to prevent damage to the hidden volume (the volume where you store your real confidential data).
So you may be wondering: Why do I have to enable protection of hidden volume when I want to store false data in the external volume (the volume where you store false data) ?
The answer to this question will seem obvious when you read the example below.
As you will see, the size of the container that will be displayed in Windows and TrueCrypt, will depend on the volume that you mount.
For example, if you mount the hidden volume, the size will be smaller than the size of the container. It does not matter because you know it's your real encrypted volume. When you store data inside, TrueCrypt will not modify data outside of this encrypted volume because it will know the size of the hidden container and where it is located.
By against, when someone force you to reveal your password, you give him the password for the outer volume and this person will have access to false information. For that person not suspect anything, the maximum size of the encrypted container will be that of the entire container file and if that person attempts to store a lot of data to fill it completely, TrueCrypt will end up write on the hidden volume. The volume will be damaged and your confidential data are lost. However, this person has never been aware of the existence of the hidden volume and it will not have to steal them.
Now you understand what is this protection. It seems clear that this protection must always be manually activated and protection is deactivated automatically after dismount
When you want to store data in your external volume, you activate the hidden volume protection and Windows will therefore not have the right to write to the hidden volume. You will see an error message appear but it does not matter because it is you who have tried to write on your confidential data unintentionally. By against, it is recommended to make copies to the external container rather than move because if TrueCrypt is blocking write a file while moving, it is possible that the moved file is lost. Once the file is completely copied, you can delete the source files.
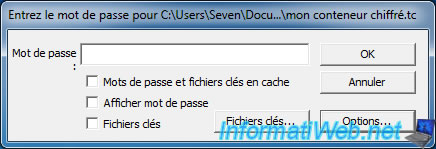
To begin, we will "mount" our hidden volume. To do this, select the container file by clicking "File" and then click "Install".
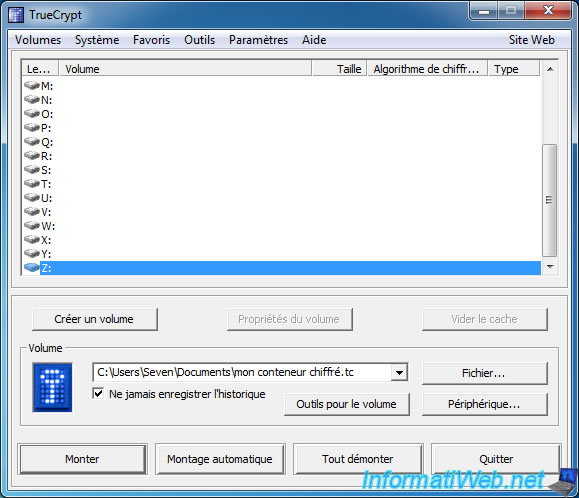
Since it is the hidden volume, simply mount it as a standard container.
Do not get confused password. In this case, it is the password for the hidden volume.
Note : Don't forget to add key files if necessary before clicking OK.
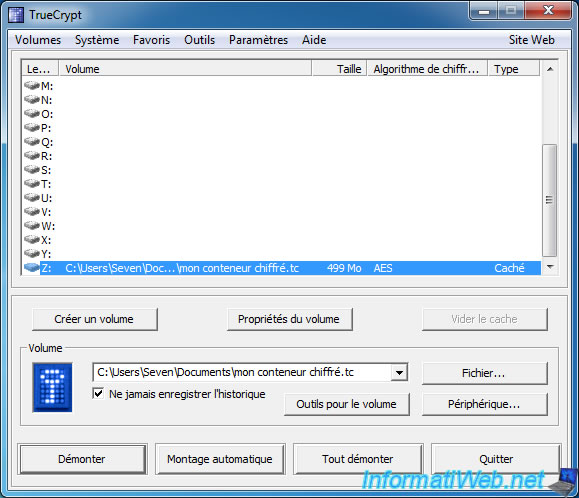
As you can see, TrueCrypt have mounted the hidden volume (which corresponds to the password that we have just mentioned) and this volume is only 499 Mo. 500 MB we have allocated for the hidden volume.
We store confidential data in our hidden volume.
Then, we dismount the volume, once we do not use longer.
Then, we will mount the external volume of our container (the volume that contains false information).
Warning : It's very IMPORTANT to start protecting the hidden volume.
To do this select your container file and click "Install".
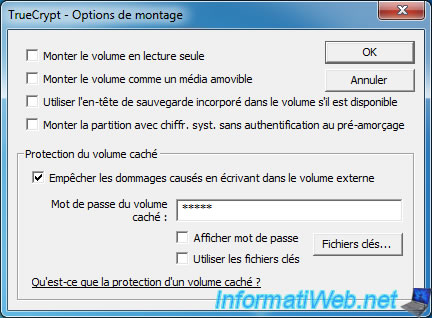
Then, click the "Mount Options" button at the bottom right.
In this window, check the "Protect hidden volume against damage caused by writing to outer volume" and enter the password for the hidden volume. Thus, TrueCrypt will know the limits of the hidden volume.
This will allow TrueCrypt to decrypt the header of the hidden volume only (without decrypting the data of the hidden volume) and may thus prevent the writing on the hidden volume.
Note : Don't forget to add key files if necessary before clicking OK.
Then, enter the password for the outer volume and click "OK".
Note : Don't forget to add key files if necessary before clicking OK.

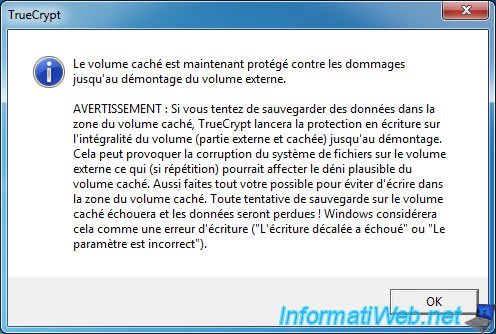
TrueCrypt confirms that the protection against damage is activated.
As you can see, TrueCrypt have mounted the External volume (which corresponds to the password that we have mentioned) and this volume has a size of 2 GB. 2 GB that we allocated for our full container. So this size includes the size of the hidden volume. That is why we have enable the protection to prevent damage to the data of hidden volume.
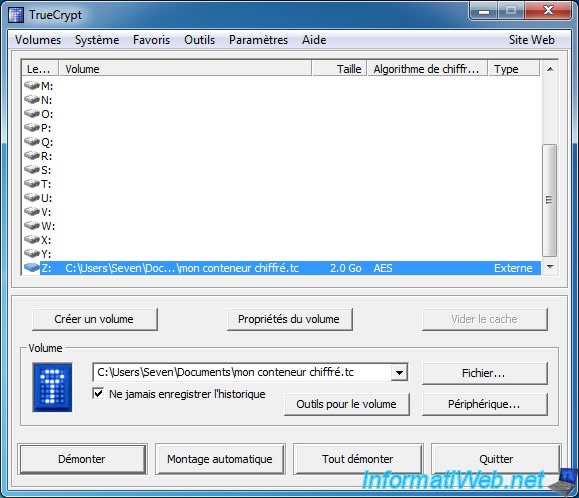
We stores false data into our external volume.
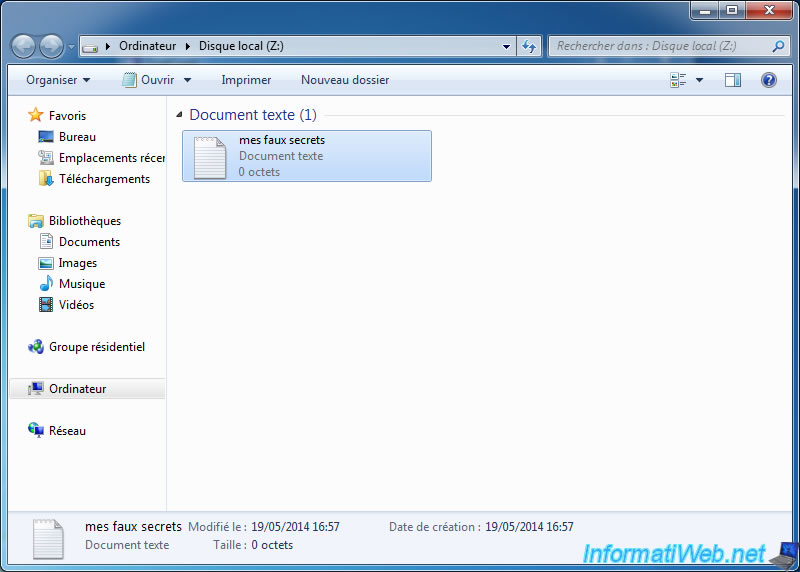
Then, we dismount the volume, once we don't use longer.
8. Optional : The emergency solution in case of absolute necessity
Finally, when someone force you to reveal your password, you give him the password of the outer volume and that person will mount it as a normal volume (because the hidden volume does not exist for elle).
Note : Don't forget to add key files if necessary before clicking OK.

As you can see, TrueCrypt have mounted the external volume in type "normal" and malicious person has no way of knowing that a hidden volume exists in this container.
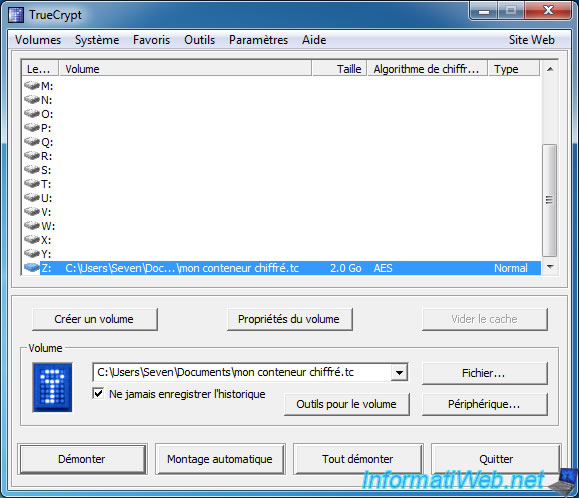
This person will see the files on the external volume and not those of the hidden volume.
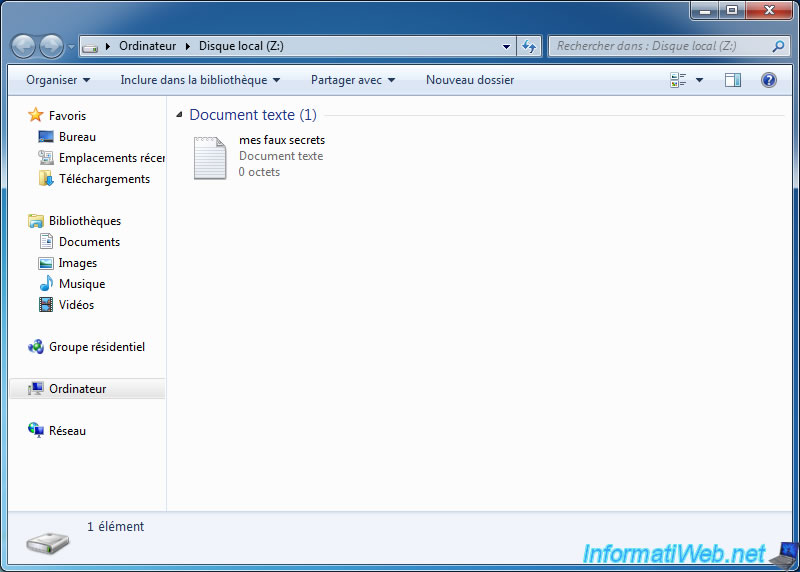
No comment