- Security
- TrueCrypt
- 22 May 2014 at 17:57 UTC
-

- 1/4
If you have sensitive information on your computer or you are using a home computer (ie, other users using the same computer as you), we suggest you to encrypt your data. Encrypt your data also prevents hackers or thieves steal your confidential data. In fact, the pirates found on the Internet are not the only malicious people. If someone steals your computer, that person will not any way access to your confidential data. If you use a strong password, your data are not at risk.
To encrypt our sensitive data, we will use "TrueCrypt" which has the advantage of being known and Open Source. This program lets you create a virtual encrypted disk where we will store our data.
It is important that security software is open-source because it allows us to know two important things :
- any virus can not be there (otherwise, the professionals have already detected)
- no bypass means exists in the code
- the data will be encrypted using a secure algorithm because it proves that this algorithm is not reversible despite that it can be read
Compatibility : Windows, Mac, Linux.
- Download and installation
- Change the language of TrueCrypt
- Create a standard encrypted container
- Mount the encrypted container to store data
- Improve the security of TrueCrypt
- Optional : Create a double container to avoid forced theft of your data
- Optional : Install the true or false encrypted container safely
- Optional : The emergency solution in case of absolute necessity
1. Download and installation
To begin, download TrueCrypt for your operating system.
In our case, we will download the Windows version of TrueCrypt.
During the installation steps, you will notice that the program can be :
- installed on the computer by selecting "Install".
- used as a portable version by selecting "Extract" option.
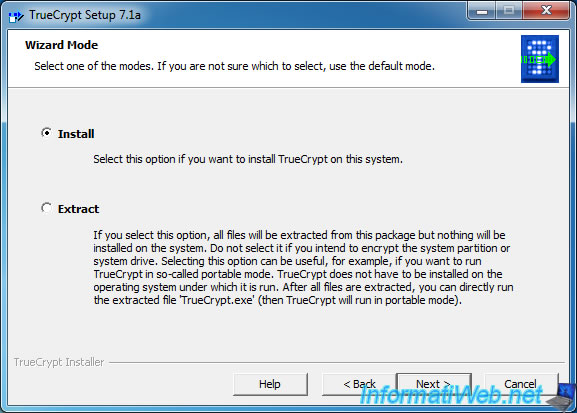
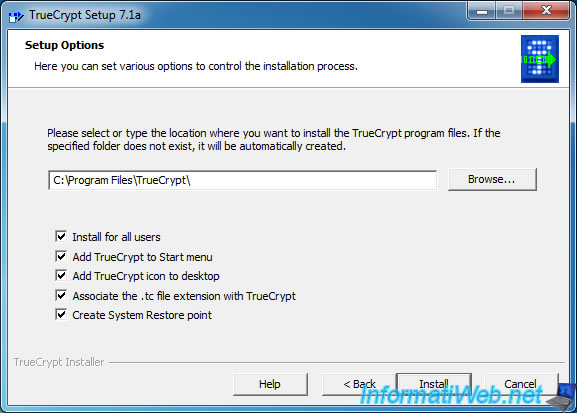
Then, you can install the program for all users of the computer or only the current user by checking or unchecking the "Install for all users" checkbox.
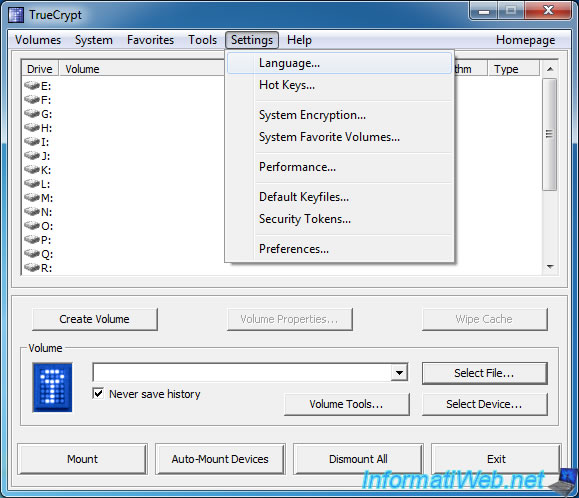
2. Change the language of TrueCrypt
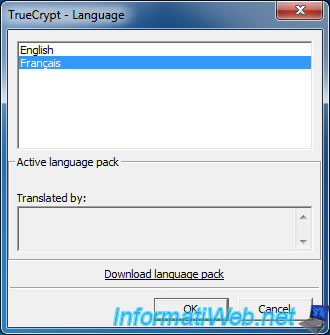
To change the language of TrueCrypt, go to "Settings -> Language" menu.
Note : The language change is only possible under Windows.
By default, only the English language is available.
To add a new language, you will need to download the desired language pack from an unofficial site (since the official website is definitely offline).
To download a new language, please refer to the link available in the "Translations" section of our TrueCrypt review.
Note : in our case, we will install the language "French".
Once downloaded language, unzip the ".zip" file and copy the files in the TrueCrypt folder. Default : C:\Program Files\TrueCrypt
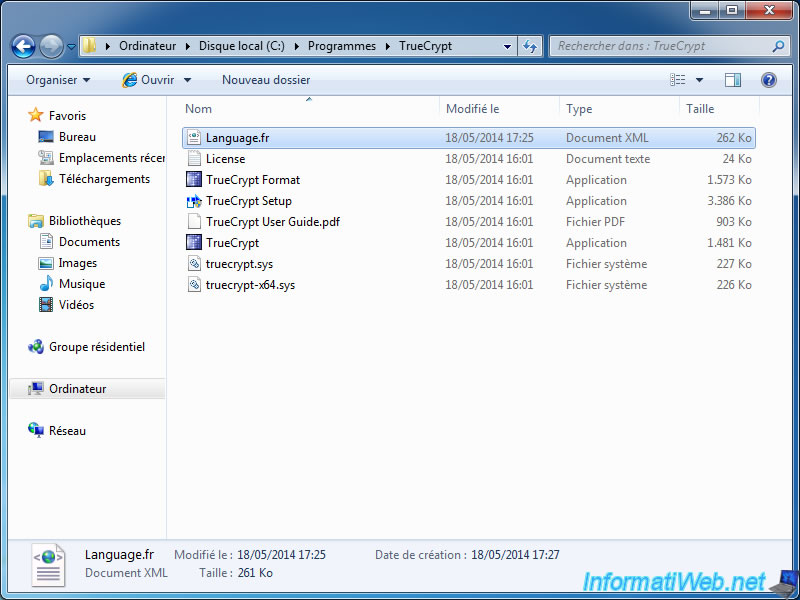
Then, return to the "Settings -> Language" menu and select your language. Finally, click "OK" to use the new language.
3. Create a standard encrypted container
Maintenant que TrueCrypt est installé et traduit dans votre langue, nous allons créer un nouveau volume chiffré.
Pour commencer, nous allons créer un volume standard où nous stockerons nos données confidentielles.
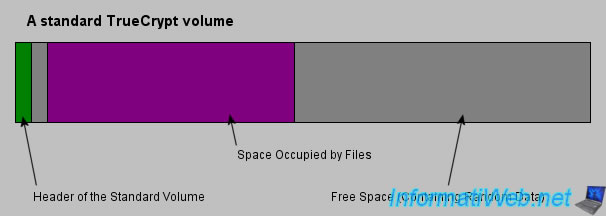
For those who wish to understand how TrueCrypt works, here is the diagram of a standard TrueCrypt volume.
As you can see in the picture below, a standard TrueCrypt volume is composed of several parts :
- Header of the Standard Volume : Information that allow TrueCrypt to know the size of the volume, the file system used, the decryption key, ...
- Space occupied by Files : Space occupied by the confidential data that you copy the encrypted volume.
- Free Space (Containing Random Data) : The free space of your encrypted volume. TrueCrypt stores random data in this space so that nobody will know what is in your encrypted volume. It also helps to completely hide the hidden volume, if you decide to create one.
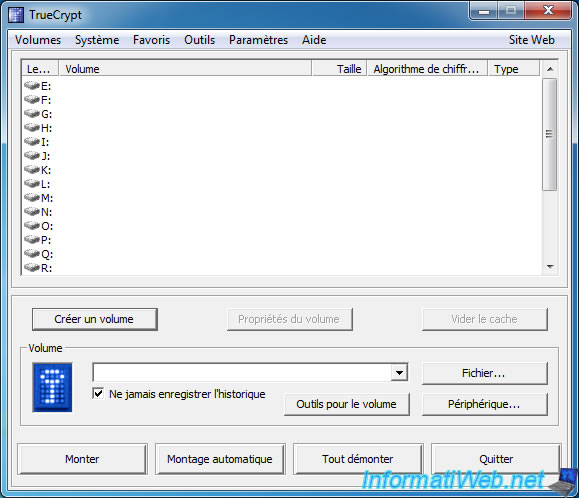
To create the encrypted volume, run TrueCrypt and click the "Create Volume" button.
Select "Create an encrypted file container".
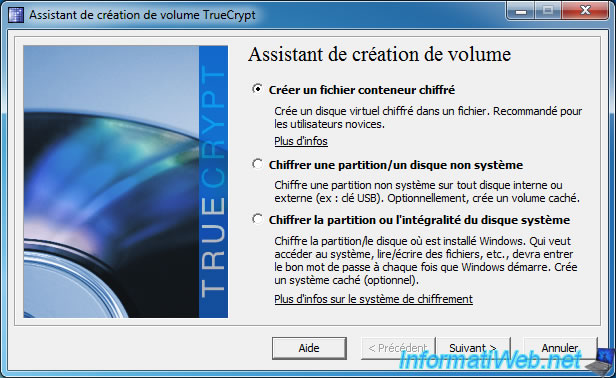
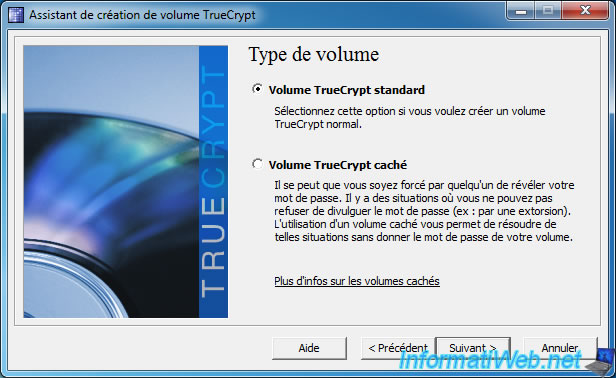
To begin, select "Standard TrueCrypt Volume".
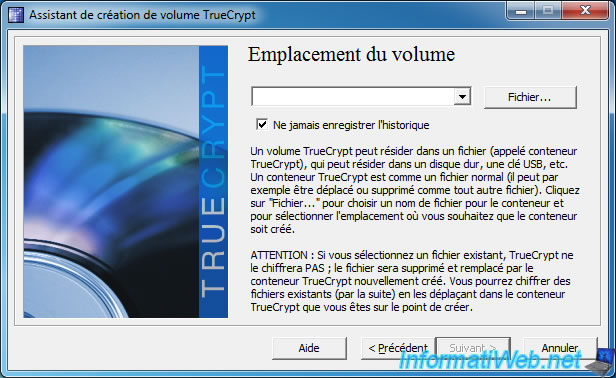
Select where you want to store your encrypted container by clicking the "Slect File" button.
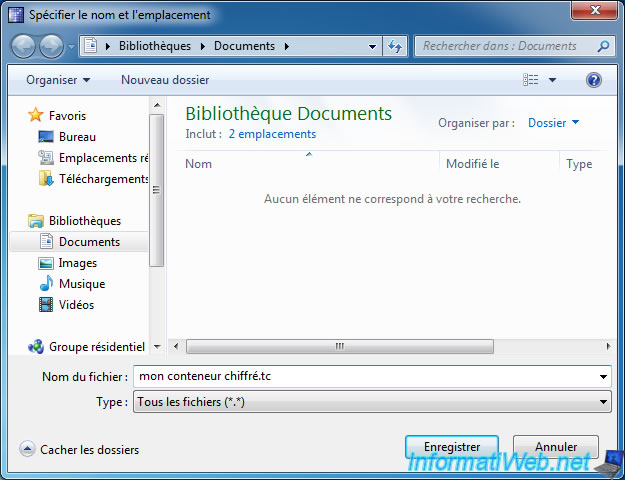
In our case, we will appoint our container file : "mon conteneur chiffré.tc".
Then, you can select an encryption algorithm.
By default, the algorithm used is "AES". This algorithm is very good and it is also used by U.S. federal agencies (as indicated by TrueCrypt).
Select the maximum size of the encrypted container.
Note : If you want to create a hidden volume within this container, specify a size larger than you want.
Because you store sensitive data in this encrypted container, it's very important to use a strong password (uppercase, lowercase, numbers, special characters and a minimum length of 8 characters).
In addition to your password, you can also use one or more key files that are a kind of very complicated password which will be required for each mounting of the encrypted container. An attacker must therefore have the correct password + the correct key file to access your data. In this scenario, an attacker will not be able to find in brute-force the 2 secure passwords to be used simultaneously.
Note :
To remember your secure password, you can use a password manager like KeePass. Don't hesitate to read our tutorial "Store your passwords securely using KeePass" if you need help with this program.
In our case, we use a secure password + key file generated randomly by TrueCrypt.
To do this, enter a password, check the "Use keyfiles" box and then click the "Keyfiles" button.
In the window that opens, click the "Generate Random Keyfile" button.
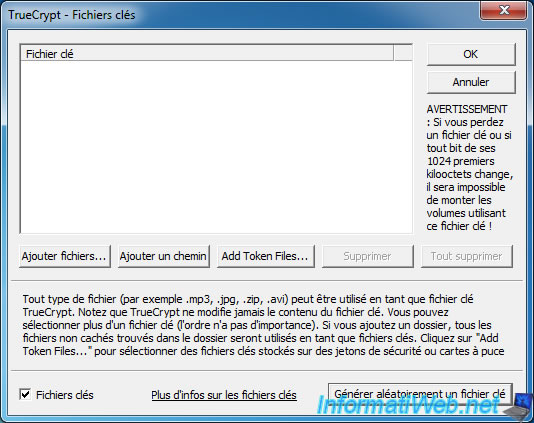
Move your mouse randomly and then click the "Generate and Save Keyfile" button.
Note : You can close this window once the file is saved.
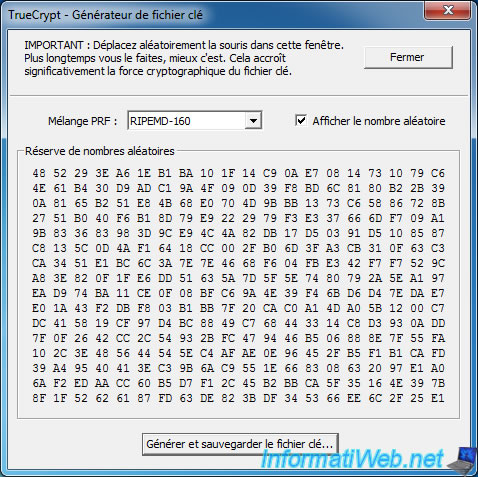
In the previous window, click the button "Add Files ...".
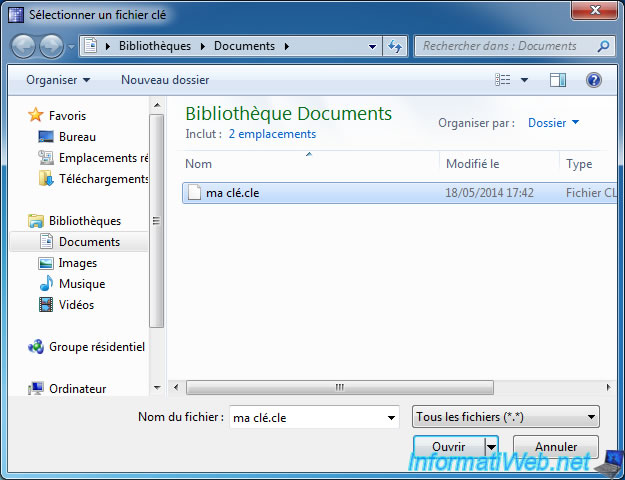
Select the key you just generated randomly.
As indicated at the beginning of this tutorial, TrueCrypt lets you create a virtual encrypted disk. TrueCrypt therefore ask you to select the file system of the virtual encrypted disk.
The FAT file system is compatible with all operating systems and NTFS is a file system from Microsoft that allows you to manage the NTFS rights, ...
To maximize compatibility, you can choose FAT but NTFS allow you to store very large files.
Concerning the "Dynamic" option, it is not recommended to use this option because it affecting the performance and it prevents you to mask your hidden container, if you decide to create one later.
Indeed, this option allows the file container to grow based on the data contained therein. If you decide to create a hidden volume within this container but let your container is in dynamic. The person who will force you to give your password will realize that the data size is smaller than the size of the file container.
If this option is not used, your container has a fixed size and the person will not be able to know that she accesses the external volume (the false volume) and not the hidden volume (where the real confidential data are)
Once you have configured these options, click on "Format" to create the file system.
TrueCrypt creates the file system.
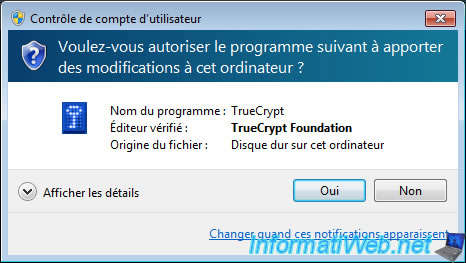
Once TrueCrypt has finished creating the file system of your container, an UAC warning will appear if you are using Windows Vista, 7 or 8.
Click "Yes".
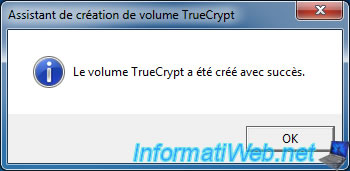
Your encrypted container is created. Click "Exit" to close the wizard.

You must be logged in to post a comment