- Security
- USB keys
- 13 June 2014 at 11:46 UTC
-

DiskCryptor is a program similar to TrueCrypt that lets you encrypt your USB drive. Once it is encrypted, everything that you store will be encrypted automatically by the program.
Important :
- The next time you plug your USB drive, Windows will propose you to format it because it does not recognize a known file system on the USB stick. Ignore this message and mount your USB stick with the program (with the correct password, of course) to use it.
- It is impossible to remove the password of your USB key as the data encryption is based on the password that you have set in advance.
- By against, you can decrypt your USB key permanently by indicating the password a last time.
- Encrypt your USB key
- Unmount your encrypted USB key to make it inaccessible without the password
- Mount your encrypted USB key for use it
- Decrypt the USB key permanently
1. Encrypt your USB key
To begin, download and install "DiskCryptor" and run it.
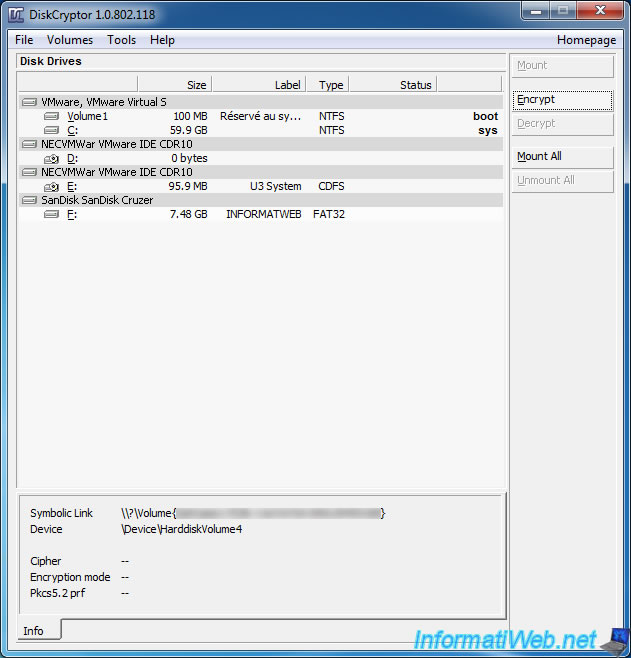
Then, to encrypt a USB drive, select the partition of your USB key from the list and click the "Encrypt" button.
Note :
- In our case, it is an USB key "Sandisk Cruzer 8GB"
- Encrypting an USB key doesn't erase the USB key first, but encrypts the data that is already there (if applicable).
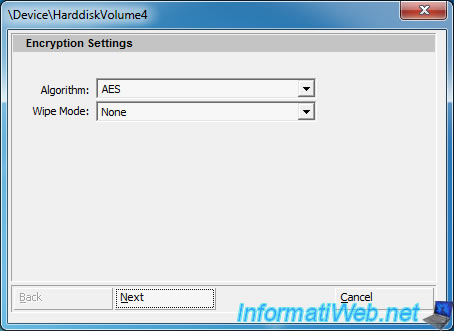
Let the algorithm "AES" as the encryption algorithm. This algorithm is very good and it is also used by U.S. federal agencies.
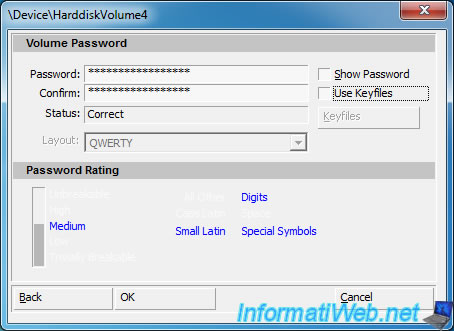
Enter a password to protect your USB key.
Important :
- Because you store sensitive data in this encrypted container, it's very important to use a strong password (uppercase, lowercase, numbers, special characters and a minimum length of 8 characters).
- In addition to your password, you can also use one or more key files that are a kind of very complicated password which will be required for each mounting of the encrypted container. An attacker must therefore have the correct password + the correct key file to access your data. In this scenario, an attacker will not be able to find in brute-force the 2 secure passwords to be used simultaneously.
- You can not store your key files on your USB key because the usb key is inaccessible without the key files. However, the use of key files is optional.
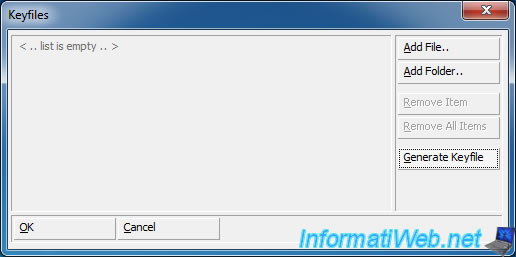
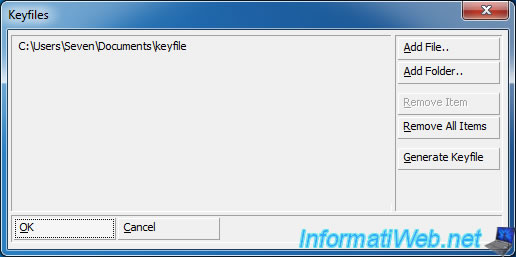
To add key files, check the "Use Keyfiles" box and click the "Keyfiles" button.
Then, click the "Generate Keyfile" button to generate a new random key file.
Save the key file where you want but don't lose this file. If you lose it, you also lose the data that is on your USB key.
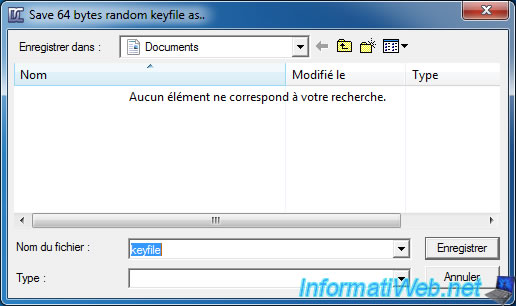
DiskCryptor will ask if you want to use this key file. Answer : Yes.
Note : With TrueCrypt you had to do it manually.
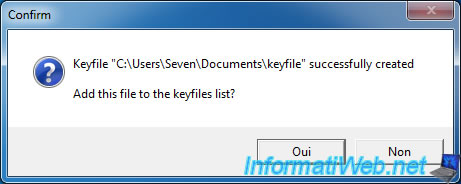
Now that the key file was created and added to the list, click "OK".
Click OK.

Then, wait while the program encrypts your USB key. The process can take a long time. Everything depends on the size of your USB key and your computer's performance.
Note : For information, encryption of our USB key 8 GB lasted for half an hour.
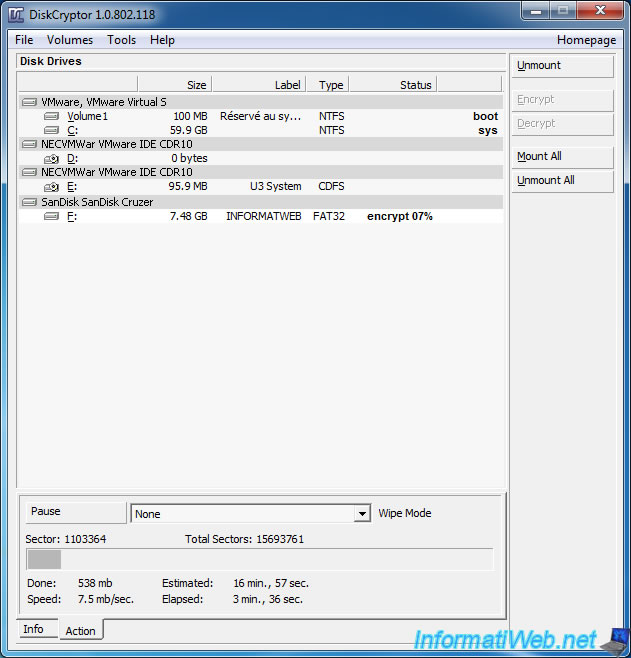
Once your USB key will be encrypted, it will be mounted automatically by the program.
As you can see at the bottom of the window, your USB key is encrypted with the AES algorithm.
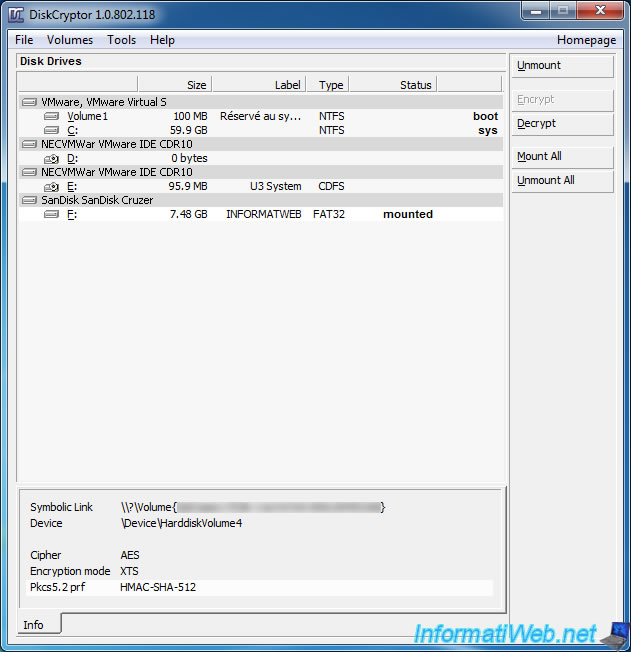
Since your key is mounted, you can access it through the workstation (or Computer in Windows Vista, 7 and 8).
Store files as you would do with a traditional USB key but do not forget to unmount it when you have finished using it.
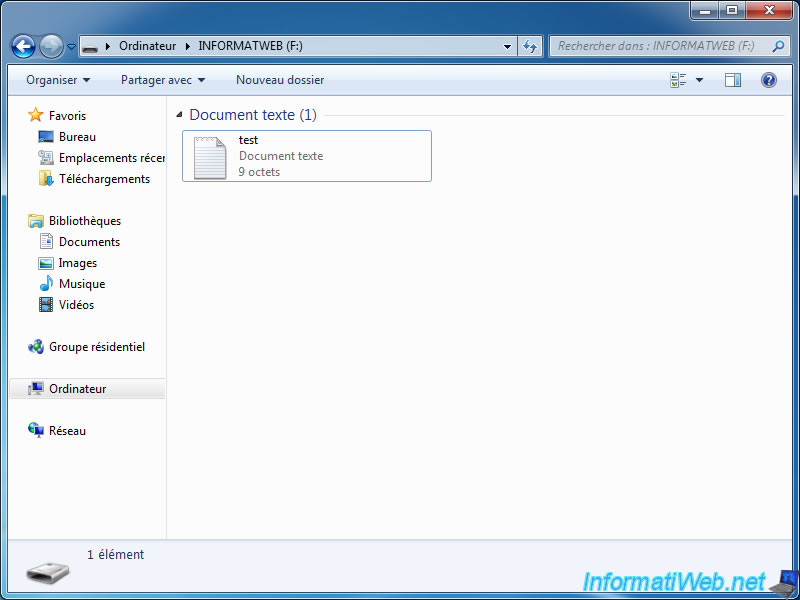
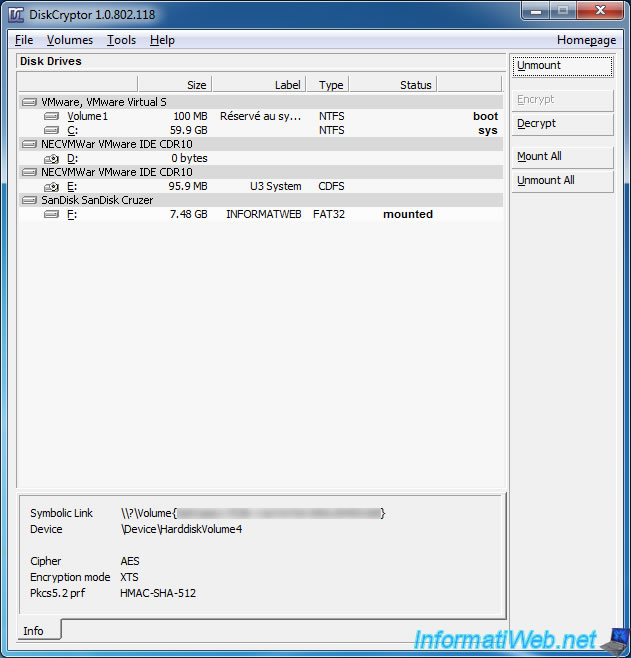
2. Unmount your encrypted USB key to make it inaccessible without the password
To unmount your USB key and make it unusable without the password (and key files, if applicable), select your USB key in DiskCryptor and click "Unmount".
Click "Yes" when the confirmation appears.
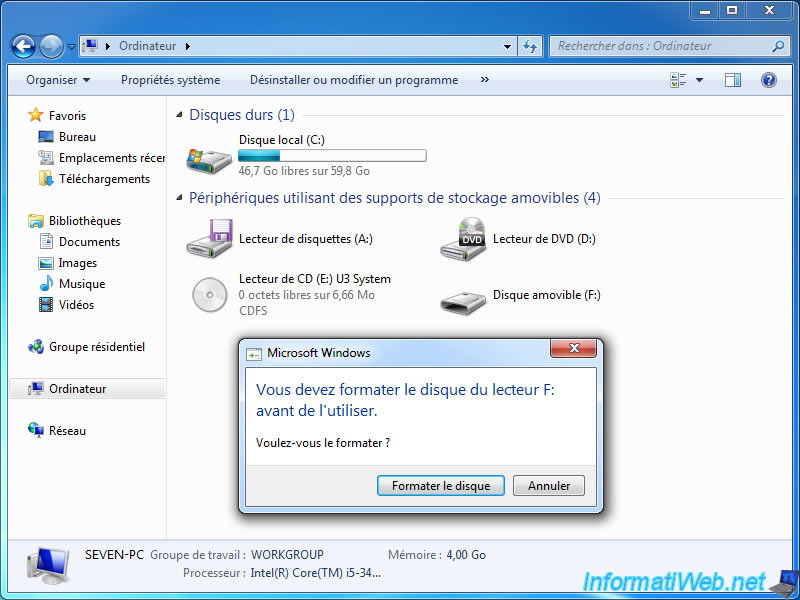
Once dismounted, the USB key is inaccessible and Windows may ask you to format your USB key.
Since the USB key is encrypted, Windows can't read the file system of the USB key and you propose to create it.
Warning : don't click on "Format Disc" as this will erase your USB key and you can't recover your data. The data recovery programs don't work because the file system of the USB key is encrypted, so it's unreadable for these programs.
3. Mount your encrypted USB key for use it
Now, when you want to use your USB key, you will first have to "mount" it by DiskCryptor.
To do this, plug your USB key and run DiskCryptor (if it's not already).
Then, select your USB key in the list and click "Mount".
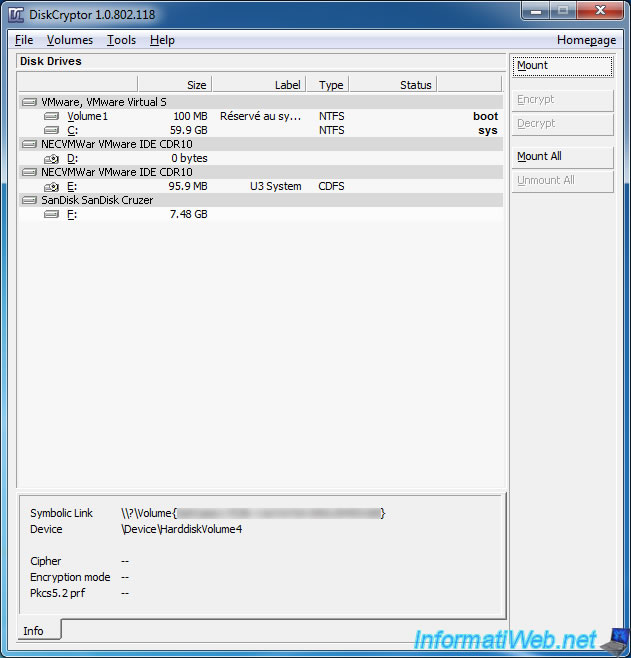
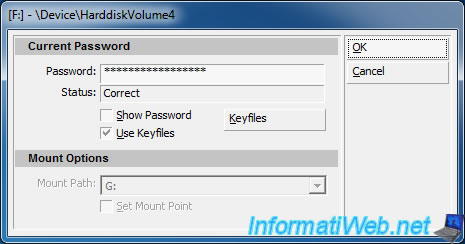
Enter your password and click "OK".
Note : If you have added one or more key files when encrypting your USB key, you must check the "Use Keyfiles" box and click the "Keyfiles" button.
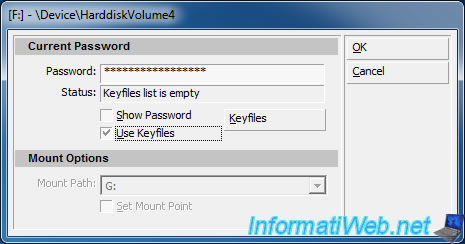
If you clicked on the "Keyfiles" button, this window will open. Click "Add File".
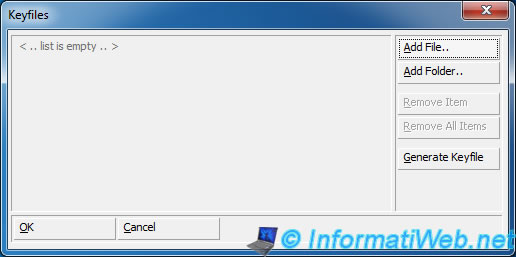
And select the key file on your hard drive.
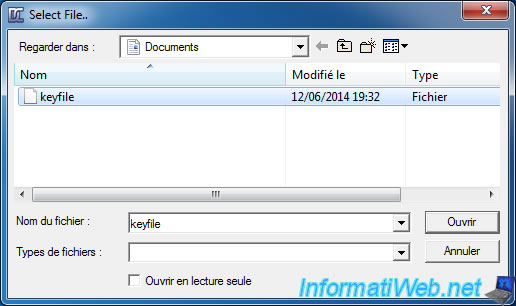
Once you have selected the key file, click "OK".
Click again on OK.
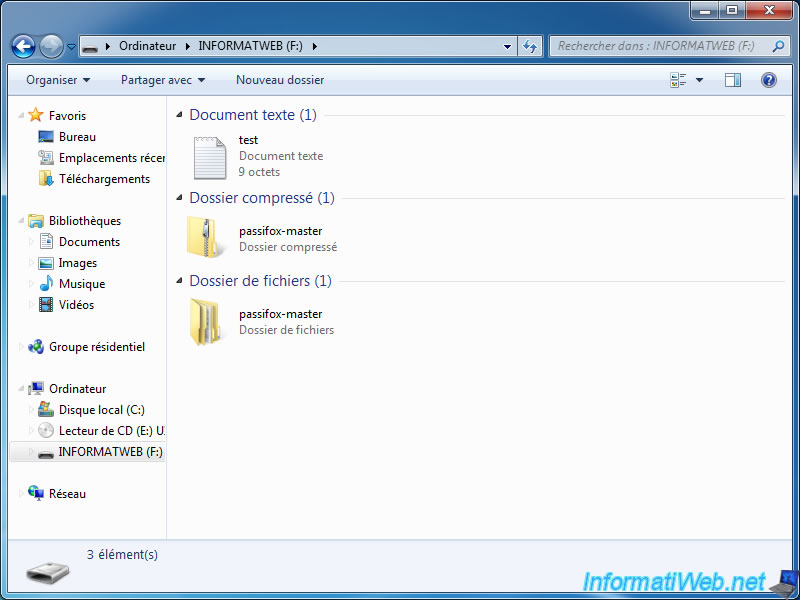
And if all goes well, you will gain access to your USB key. The status of the USB key will change to "mounted".

Now, you can store data on your encrypted USB key.
4. Decrypt the USB key permanently
If you want to permanently decrypt your USB key, you will need to mount it and click "Decrypt".
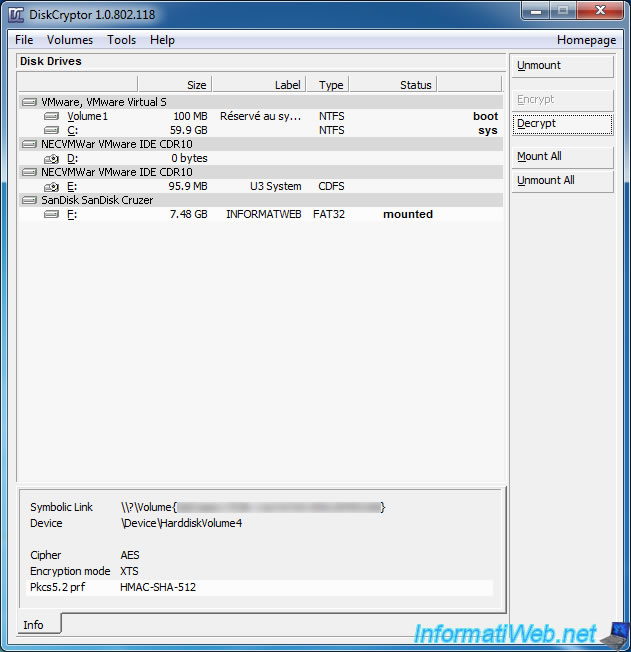
For safety, the program will ask you a last time your password (and key files, if applicable).
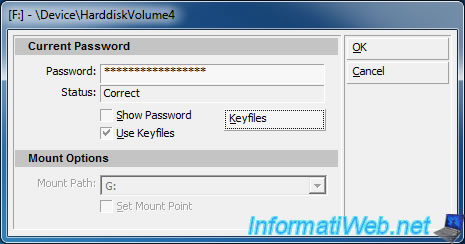
Then, wait while the program decrypts your USB key. The process can take a long time. Everything depends on the size of your USB key and your computer's performance.
Note : For information, decrypting our USB key 8 GB lasted for 42 minutes.
Share this tutorial
To see also
-

Others 9/18/2012
Create a bootable USB key
-

Articles 2/8/2017
Kingston DataTraveler Locker+ G3 - Secure USB key
-

Articles 11/2/2014
Some practical infos about USB storage devices
-
Windows 9/9/2024
Test and repair an USB key in a software way

Thank you for your hints.
You must be logged in to post a comment