Protect yourself against viruses, hackers and traps present on Internet
- Security
- Avast, KeePass, MBAE, MBAM, USB Vaccine
- 12 March 2016 at 14:09 UTC
-

- 4/5
15. Don't fall into traps present on Internet
15.1. Spams
You will perhaps not know it, but about 170 billion spam messages are sent every day.
To identify spam, there are several methods :
- looking for a part of the content of the email on Internet (Google is your friend)
- search for the title of the email on Internet (ex : coca cola lottery, Your PayPal account has been limited, ...)
- check the link in the email. In case of doubt, look for the name of the official website in Google and you will find true address.
False addresses are sometimes IP addresses in the format "123.456.789.012" or bogus domain names that redirect you to a malicious site. (Often hosted in a country far from yours.)
And elsewhere it is always the same. Examples of spam :
- replies to emails that you never sent
- e-mail with an attachment sent by an unknow person. (so, a virus)
- the name of someone you know is displayed as the sender, but the e-mail address doesn't match
- you won a lottery that does not exist. The best known concerns Coca Cola that was never create some lottery.
- Your PayPal account has been limited. Message totally false and that PayPal will never send
- there is a problem with your VISA card (while you don't have some VISA card, or not in the bank indicated by the spammer)
- you have not paid your Movistar bill of xx/xx/xxxx. (Except Free, doesn't exist in your country)
- Same with Orange, ...
- the spammer pretends to be Hotmail, Yahoo, your bank, your telecom operator or another and asks you for your user name (nickname), your password, ...
This kind of email is completely false. All system administrators and developers (PHP in particular) will tell you.
An account is a line in a table stored on a server. And the administrator or developer can access to your account information with the account administrator or root (on linux) of the server. In this case : MySQL, SQL Server or other similar servers.
In short, your bank, ... will never ask you for your password, because they do not need it and it can even change it if they want. - une personne vous parlant de prêts entre particuliers ou d'un héritage d'une personne décédée ou qui va bientôt mourir.
Information about fake mails about Paypal :
- if you have a hotmail, outlook.com, msn.com, live.com, ... address. Know that Hotmail still shows a small green shield next to real messages sent by PayPal.
However, a spammer had succeeded to send a fake Paypal email with another small green icon in the title. So, beware. - If you receive a fake email about Paypal or you have any doubt about the email received, transfer the mail to spoof@paypal.com
It will allow them to lead their small investigation.
15.2. Fake advertisements, fake antivirus, ...
15.2.1. Fake advertising
Among banners and popups (pop-ups that open by themselves), you will see some of these fake advertisements :
- "It's not a joke. You are the 100,000th visitor of the day"
- "x virus were found on your computer" or "Your computer may be infected"
- "Your PC is slow" or "Slow computer ? Perform a free scan ..."
- "Your PC is about to crash"
- fake updates for flash or other known programs.
- know who has blocked you on MSN or Facebook (they only steal your password)
Here are some screen shots of these fake advertisements :
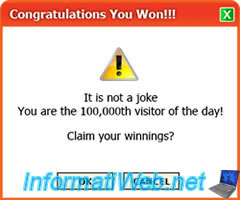
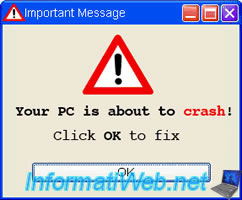
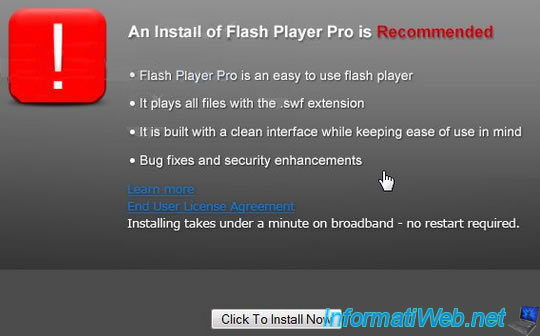

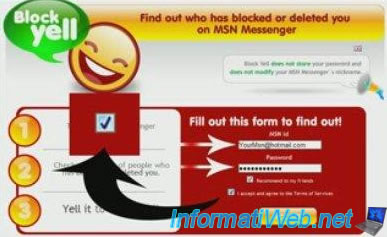
15.2.2. Malicious sites in Google ads
In the same style, but lesser known, there are also malicious sites show in ads of the famous search engine Google.
If Google displays malicious sites in its ads is because one or more hackers have paid Google (via Google Adwords) to distribute a sponsored link at the top of Google results.
When a person goes through Google Adwords, she can choose keywords for its advertising.
Thus, if the user search "trip", he will have ads or commercial links (which is the same) that redirect to tour companies such as Voyage SNCF, Opodo or Neckerman.
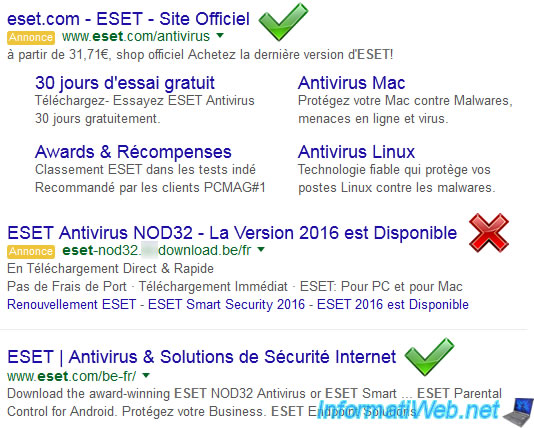
In the case of the hacker, he will choose for example "NOD32" and "ESET" as keywords for the user falls into his trap and download the infected version instead of downloading the program on the official website.
As in this example tested in January, 2016.
Note : we added some "v" green and a red cross to show which links are reliable and which is not.
Indeed, "www.eset.com" and sub-domains of "eset.com" belong to the true good company "ESET". The author of the antivirus "NOD32."
Except, that the link "eset-nod32.a-fake-domain.com/en" redirects to a subdomain "eset-nod32" of a hacker site whose domain is ".... download.be".
15.2.3. Fake antivirus
Finally, with fake advertising and fake programs offered on Internet, there are also fake antivirus.
These are programs created by hackers, who look like antivirus.
Generally, these programs :
- are installed aotumatically without your consent (because of a virus present on your computer)
- removes your current antivirus without you ask. You will notice that your antivirus will disappear by itself to make place for the fake antivirus of the hacker.
- plant your computer. They detect Windows files as viruses. Sometimes, they detect the "Windows" folder as a virus. Which is absolutely fake
- are impossible to uninstall or appear again by themselves if there are poorly removed
- sometimes offers to buy the paid version of the infected program. One way to make money without the knowledge of the user.
- will perhaps offer other fake programs to "optimize your computer." In reality, they will plant the PC even more than before.
Here are some screen shots of the fake antivirus :
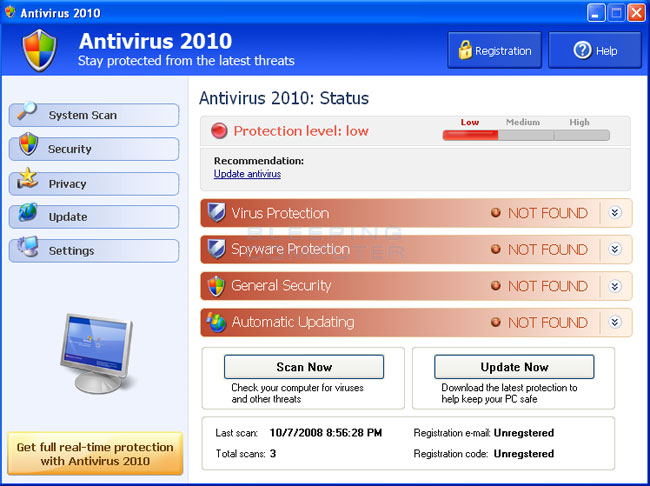
Including an antivirus that detects the "C:\Windows" folder as a "Trojan Downloader".
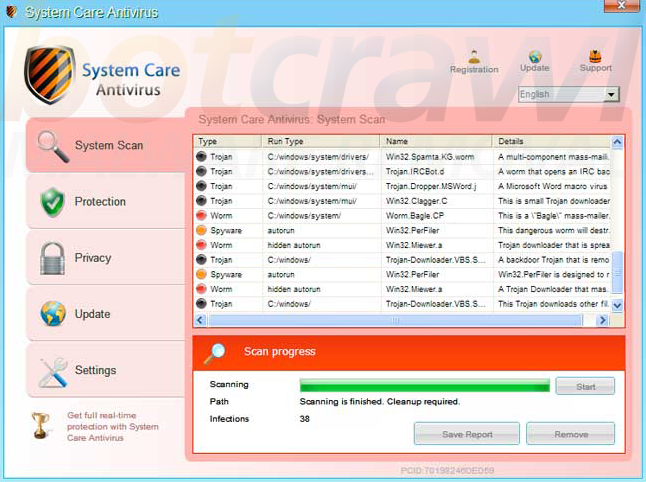
In short, to uninstall this type of fake antivirus, look for "remove + his name" with Google to find how to remove it completely.
And never buy the paid version of one of these programs. This will be useless.
16. Never download an attachment sent by an unknown person
This may seem logical for some users, but others will be curious and open certain file types.
Indeed, most people think that a virus is necessarily an exe file. But, in reality, a virus can be in any file : programs (exe), documents (txt, doc, docx, pdf), music (mp3, flac), videos (avi, mp4, ...) or other file types.
Anyway, if a unknown person sending you an email with an attachment, don't open it. Don't open the mail and do not open the attached file.
For information : "e-cops" and "cryptolocker" ransomwares were sent notably by email.
In some cases, these malicious emails are sent with the same name of a person that you know. In such cases, check that the email address of the sender matches the real e-mail address of your friend.
If it does not the case, it's a spam. So, don't open the attachment.
Finally, this kind of mails :
- is written in poor French (we realize that this is a translation and the sentences are poorly written)
- are in English
- sometimes empty. There is an attachment with no text in the email. Which is very suspect.
- sometimes come into the junk or spam folder
In case of doubt, send a new email to the person indicated as sender or better, contact your friend via another site. Examples : social networks, phone or other.
So, even if a hacker really hacked the e-mail address of your friend, she will tell you that she is not at the origin of the email that you received.
17. Protect accounts with 2-step verification
In recent years, the known sites like Gmail, Facebook, ... have strengthened their security.
Now, most of known sites offer the 2-step verification.
What is the 2-step verification ?
This allows you to connect to a site by specifying :
- your username or your email address (depending on the concerned site)
- your password
- + A unique code that you receive by SMS (generally, it's free)
Generally, this protection is disabled by default.
Why enable it ?
To better protect your Gmail account, Facebook acoount or other.
Indeed, once enabled, the person who wants to connect to your account should know :
- your username or your email address
- Your password
- and if he knows these 2 information, he should also specify the unique code that you received via SMS
This means that even if a hacker has steal your credentials "Username + Password" with a virus on your computer, the site does not give him access to your account because he will not know the unique code that you received on your mobile phone or smartphone.
Moreover, if you receive an unique code from Google or other while you have not tried to sign in to your account, you'll know that someone knows your password.
So, you can simply change it.
IMPORTANT : Never give this unique code to someone, even if it is being requested. The person who asked you this kind of thing can only be a pirate. Even if he said be part of Google.
As I said earlier in this article, the site on which you have an account never need your password or an unique code. Moreover, they are the ones that we sent you this code, so it is completely absurd that they request this code just after.
How to enable it ?
- For Google (including gmail, Google+ and Youtube) : Turn on 2-Step Verification
- For Hotmail, Outlook, MSN, ... (Microsoft) : About two-step verification
- For Yahoo : Two-step verification for extra account security
- For Facebook : What are login approvals? How do I turn this setting on?
- For Twitter : Using login verification
Share this tutorial
To see also
-

Security 2/19/2016
Avast Free Antivirus - The best antivirus
-

Security 5/5/2014
KeePass - Store your passwords securely
-

Security 2/29/2016
Malwarebytes Anti-Malware - The best anti-malware
-

Windows 12/3/2012
Prevent the spread of viruses by USB supports
No comment