Protect yourself against viruses, hackers and traps present on Internet
- Security
- Avast, KeePass, MBAE, MBAM, USB Vaccine
- 12 March 2016 at 14:09 UTC
-

- 5/5
Secure your Internet connection by using VPN servers
18. Secure your electronic payments
To secure your online payments, there are several complementary possibilities :
- One provided by your bank : card reader or digipass.
- The one you can install : Internet Security solution with protection of online payments
- Check that you are on the official website, not a counterfeit (phishing)
18.1. The card reader or the digipass
If you want to make payments online, all known banks provide you a card reader or a digipass.
In 2 cases, the principle is to send an unique code that corresponds to your account (at the bank).
Without this unique code, it's impossible to access your account.
For example, for the card reader, you can log into your bank account (via PC banking) like this :
- Specify your account number + your client number
- insert your bank card into the card reader provided by your bank
- type your PIN code and the random code displayed on the site
- the card reader will show another unique code that you will have indicated on the site
- If all information matches (account number, client number and unique code), you can log into your bank account. Otherwise, the connection will be denied.
18.2. Internet Security solutions with protection of electronic payments
Some Internet Security solutions provide :
- a feature designed to protect your online payments
- an extension ensuring that you are not on a spoofed site (a counterfeit, phishing, in short : a fake site created by a hacker)
- a secure browser isolated from the system that you can use to avoid spyware that record keystrokes, ...
For example, Kaspersky Total Security 2016 provides a "Safe Money" feature that is an extension that is installed in your web browser.
This extension will protect you against :
- Copies of the clipboard
- the screen shots
The hacker will not be able to recover an account number that you have copied/pasted, or recover an account number, unique code, ... displayed on the screen.
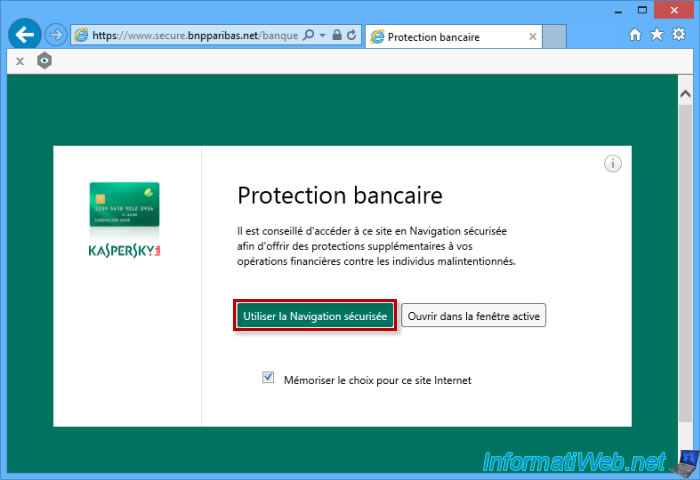
Another example : Avast Internet Security provides a feature called "SafeZone".
SafeZone is a secure web browser based on the Chromium project (on which Google Chrome is based).
On top of that, the SafeZone web browser :
- does not store the browsing history.
- block ads of websites
- opens sites considered suspicious or dangerous in a protected window.
If you use the "Pay" mode of SafeZone :
- the browser will be isolated from the system. The keylogger of a hacker will not be able to steal account numbers, unique codes typed on the keyboard, ...

18.3. Official site or phishing ?
To be sure you are on the official website of your bank, you need to check the address in your web browser address bar.
In the address displayed, you should check :
- she begins with https and that the certificate is valid. If this is not the case, the "https" is shown in red and/or the web browser will display a warning before access to the concerned site.
- the domain of the site you want to access.
Examples :
- "ing.be" and "www.ing.be" link to the real ING website.
- But, "ing.a-fake-domain.com" does not belong to ING. In this case, "ing" is a subdomain of the domain "a-fake-domain.com" created by a hacker. - in some cases, banks use a SSL certificat with extended validation. In this case, the bank's name may even appear in green at the beginning of the address.
As the name "ING Luxembourg S.A. (LU)" in the image below.
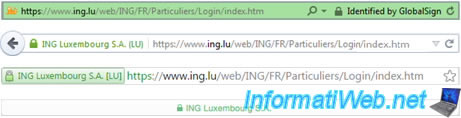
Note that a hacker could not ask for a SSL certificat to a trusted certification authority , because the authority will check the information requested by the hacker and deny the request because he is not the owner of this bank.
Note that a hacker can not secure its phishing with a SSL certificate , because certification authorities refuse his request.
Indeed, the certificate must come from a trusted certification authority such as Verisign or GeoTrust , to be valid.
Before providing a SSL certificate for a site, the certification authority should ensure that :
- the person is the owner of the concerned domain
- he's not a phishing website of a known site or bank
- etc.
Thus, a certificate request for a "fake-paypal-site.com" domain will be rejected because this website constitutes counterfeiting of the official site : paypal.com.
19. Make backups of your data
To complete this complete article about the security of your computer, we will finish with the interest to make backups of your data.
Indeed, data of a computer can be infected by viruses or other malware. Or be lost if your hard drive fails, for example.
For data backup, there are several possibilities :
- backups to the cloud. Examples : Dropbox, Google Drive and Hubic*
- local backups on external hard drives, USB keys, ...
* When registering on Hubic, remember to specify the "GYEBKA" code in the "You have a referral code ?" box.
19.1. Cloud backups
They have several advantages, but also disadvantages.
Indeed, advantages are :
- you can access your data from any computer, smartphone, tablet, ... if it's supported by the provider used. This is particularly the case for Dropbox and Google Drive.
- you get a free storage space on Internet
- your data are protected against possible theft that a thief would perform physically at home. Theft of your computer, ...
Obviously, there are also disadvantages :
- if a hacker hack your account, the hacker will have access to your saved data in the cloud. In Google Drive, simply activate the 2-step verification for Google to avoid this inconvenience.
- these solutions are free, because you are the product. Indeed, your data are stored on servers of very known companies like Google or OVH.
- violations of privacy and resale of information about you. This isn't new and Facebook, Google, ... do it too.
- your data can be lost if servers where your data are hosted would come to fail. Typically, your data are protected by RAID volumes, but this protection is not 100% reliable. Especially when the service is free.
- depending on the size of data to transfer and the upload speed of your Internet subscription, time to save your data online can be long.
19.2. Backups on external hard drives, USB keys, ...
This type of backup has its advantages and disadvantages.
Advantages are:
- a larger storage space. Indeed, we can find external hard drives of 500GB, 1TB (1000GB), 2TB (2000GB), ... at affordable prices
- a faster transfer speed. USB 2 is faster than USB 1 and USB 3 is faster than USB 2.
- you do not rely on an online service
- your private data stay at home and aren't on servers of Google or others.
Disadvantages are :
- a hard disk may be defective.
- the external hard drive can be lost or stolen
- data of an external hard drive can be infected by viruses when you connect it to the computer
Finally, if you want to back up your data securely, know that it is possible to find boxes for external hard drives that encrypt data on the fly.
So, when you connect the external hard drive through this case, your computer will be able to read data only if you type the correct password on the case.
In our case, we use the case "SecuPort-DA-74000" from Digitus, bought on LDLC as you can see in their comments.
However, if you don't find this product on the Internet, you can also buy the "Zalman ZM-SHE500" or "StarTech S2510BU33PW" casing which are almost identical.
In the same style, there are also encrypted USB keys. Depending manufacturers, the code must be typed on the USB key or by a program provided by the manufacturer of the secured USB key.
20. Secure your network / Internet connection
We use a lot of online services, and the potential risk of data theft by hackers is becoming greater.
To solve this problem, simply encrypt your network and Internet connection through paid VPN servers : Secure your Internet connection by using VPN servers
Share this tutorial
To see also
-

Security 2/19/2016
Avast Free Antivirus - The best antivirus
-

Security 5/5/2014
KeePass - Store your passwords securely
-

Security 3/6/2016
Malwarebytes Anti-Exploit - Protection against zero-day
-

Security 2/29/2016
Malwarebytes Anti-Malware - The best anti-malware
No comment