- Backup
- Acronis True Image
- 25 August 2025 at 13:15 UTC
-

- 1/4
Thanks to Acronis' support for blockchain (via its free Acronis Notary service), you can now back up folders and/or files by automatically authenticating them via blockchain with Acronis Cyber Protect Home Office (True Image).
This allows you to ensure that the files contained in your backup have not been manually altered, as well as to be able to prove that you are the first to have created a particular file.
This can be useful to prove that you are indeed the author of the file in question, because you authenticated it before the other person.
Warning : the automatic generation of certificates on the Acronis Notary service can take a little time.
It is therefore not possible to directly verify the authenticity of a file right after the backup, it can take more or less time, probably depending on the number of files to be authenticated and also the workload of Acronis Notary. Nevertheless, you just have to wait.
- Configure backup to authenticate your files via blockchain
- Backup and authenticate the folder to be saved
- Certification in progress
- Verify file authenticity via Acronis Notary Console
- Verify the authenticity of a file from Acronis Cyber Protect Home Office (True Image)
- Restore authenticated files
1. Configure backup to authenticate your files via blockchain
For this tutorial, we have stored 3 different files in our personal downloads folder.
The goal is to show that not all file types will be authenticated by Acronis (even if they will also be backed up) and that one of the techniques for verifying the authenticity of a file is limited to 1 GB per file.
Hence the presence of an ISO file of less than 1 GB and the other of more than 1 GB.
Rest assured, files larger than 1 GB can also be verified using one of the techniques available in Acronis Cyber Protect Home Office (True Image).
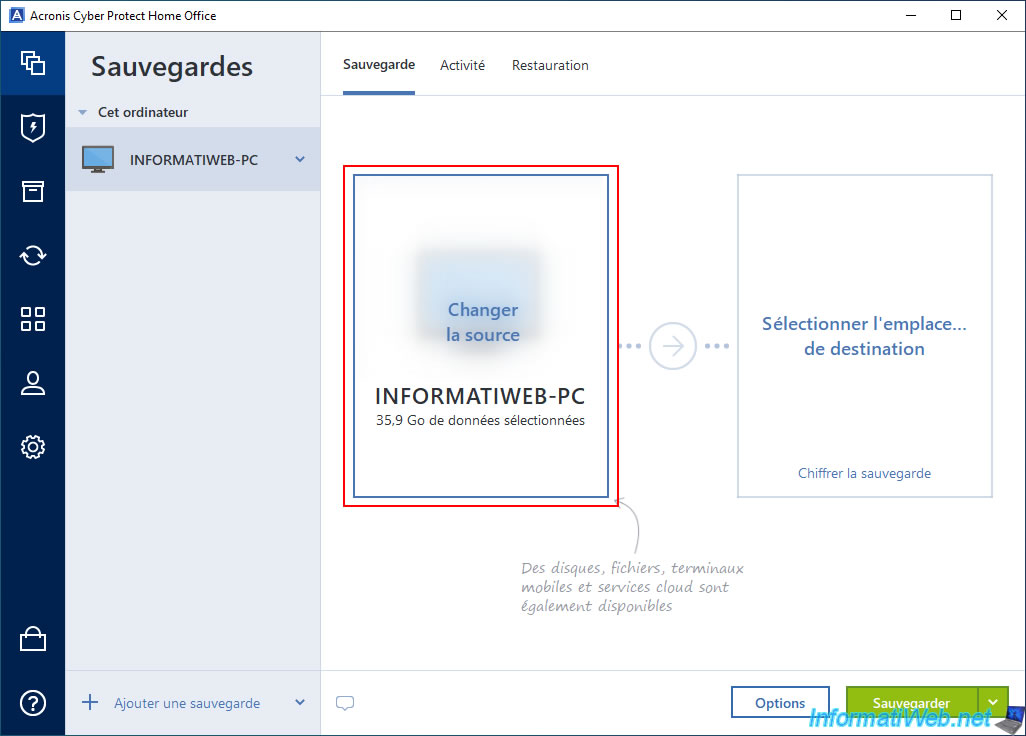
In Acronis Cyber Protect Home Office (True Image), go to the "Backup" section and click on the left image to change the source.
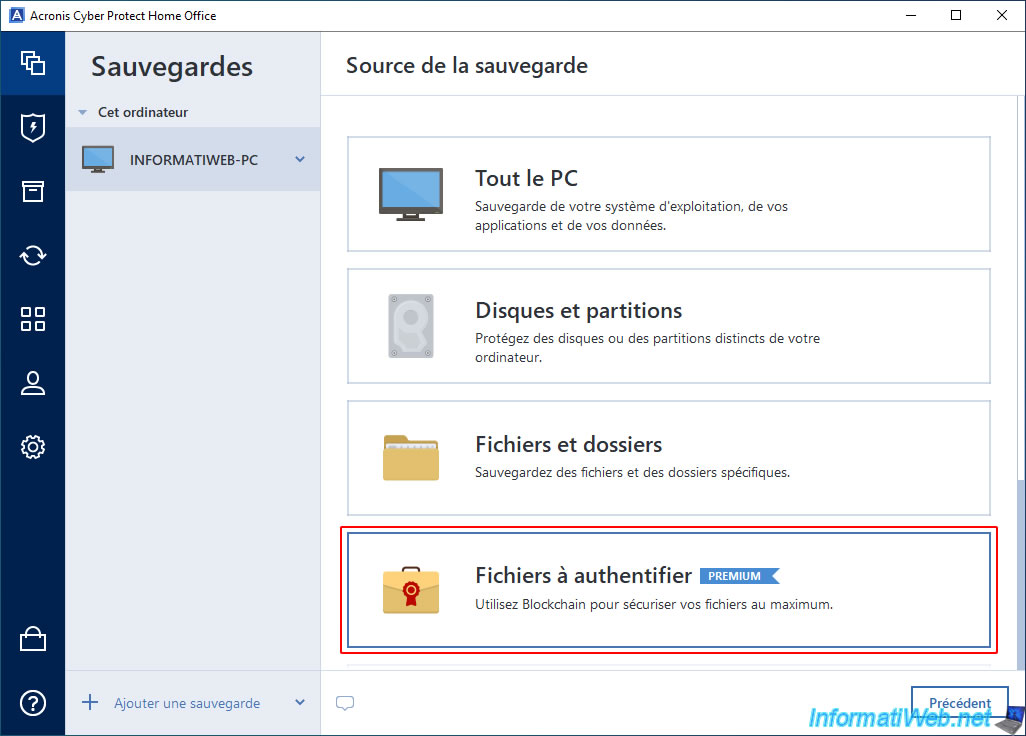
In the "Backup source" list, choose "Files to authenticate".
Important : as you can see, this is a Premium feature.
So it requires a Premium subscription to Acronis Cyber Protect Home Office (True Image).
Source: The best data protection tools | Acronis True Image Premium.
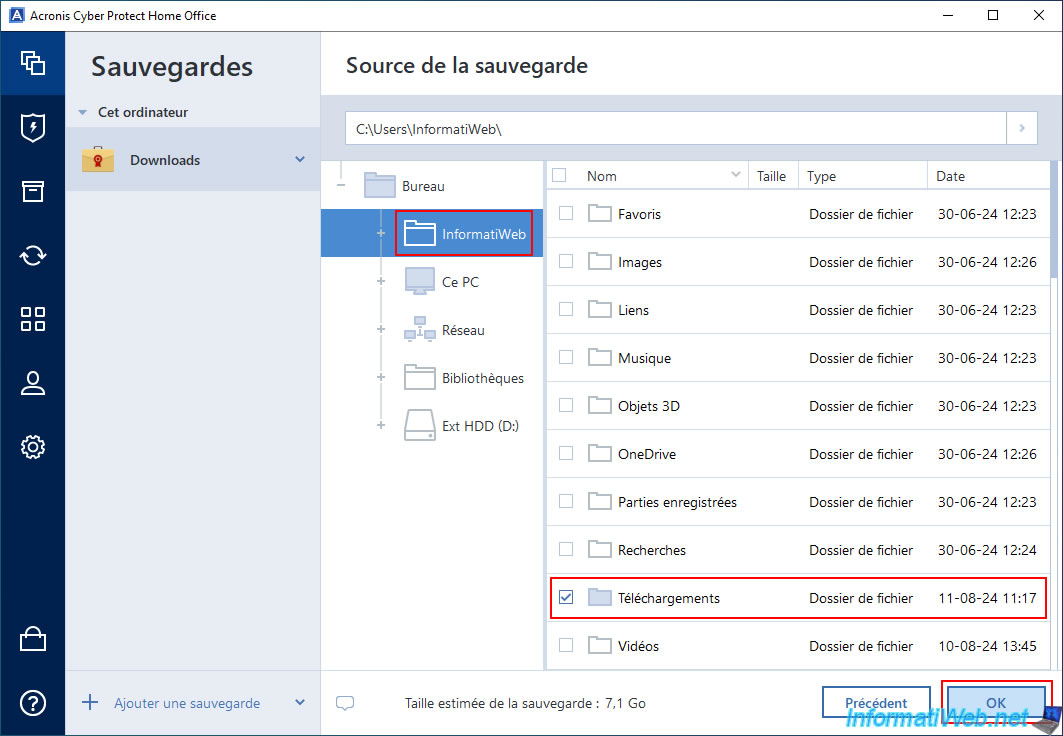
Check the boxes of the folders you want to backup and therefore you want to authenticate the files.
In our case, our personal "Downloads" folder.
Then, click OK.
As you can see, a special icon with a medal (which is often the case when using certificates) will appear for the backup source.
Now, click on the right rectangle to change the backup destination.
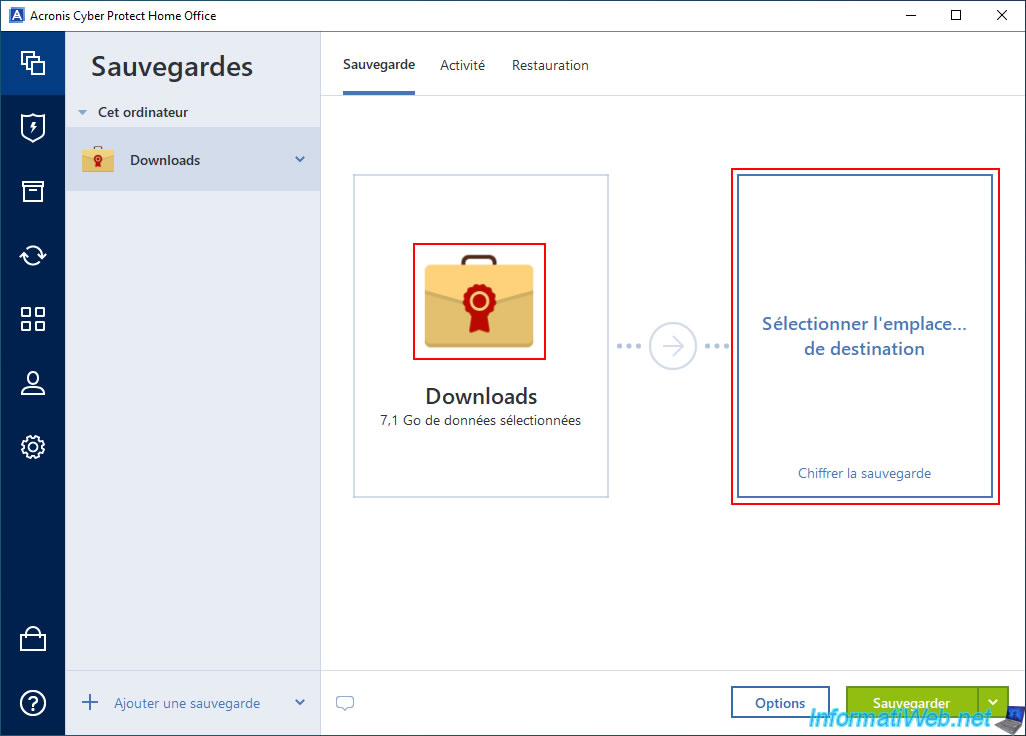
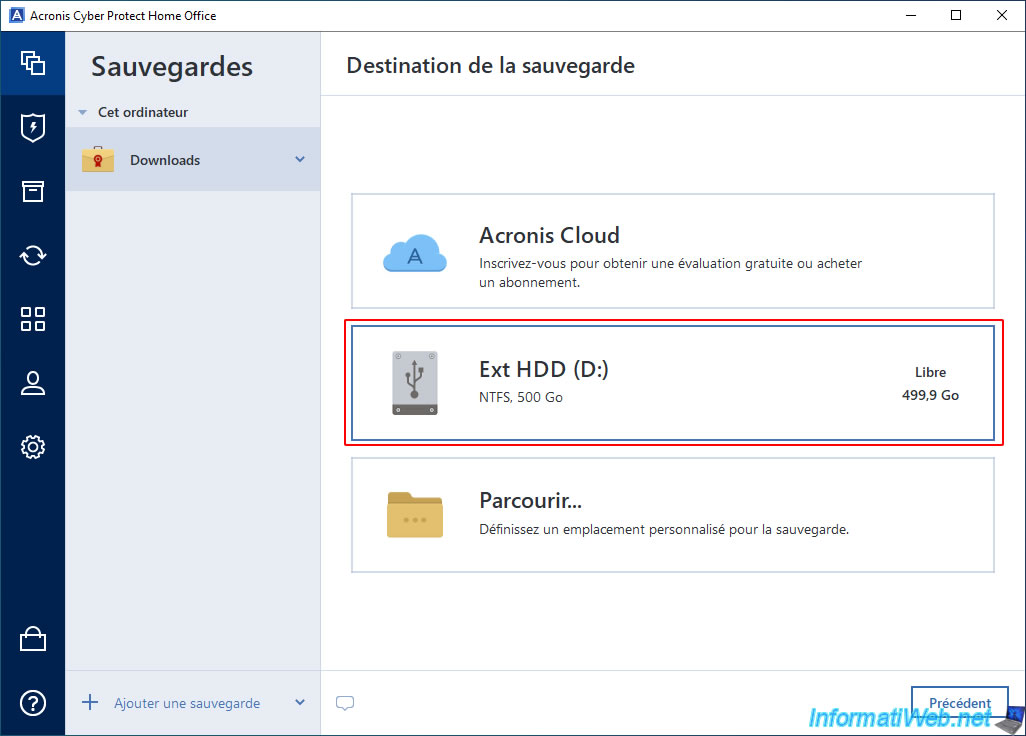
In our case, we will save this folder to our external hard drive.
Backup with authentication via blockchain is configured.
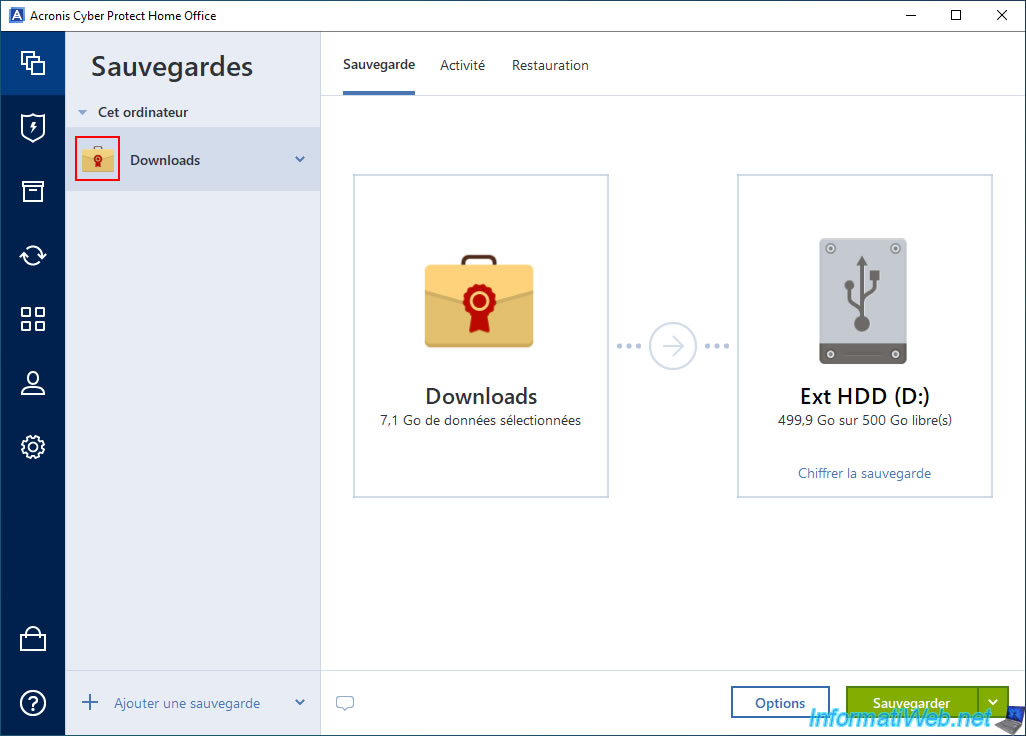
2. Backup and authenticate the folder to be saved
Now that the backup setup is done, click the "Backup" button.
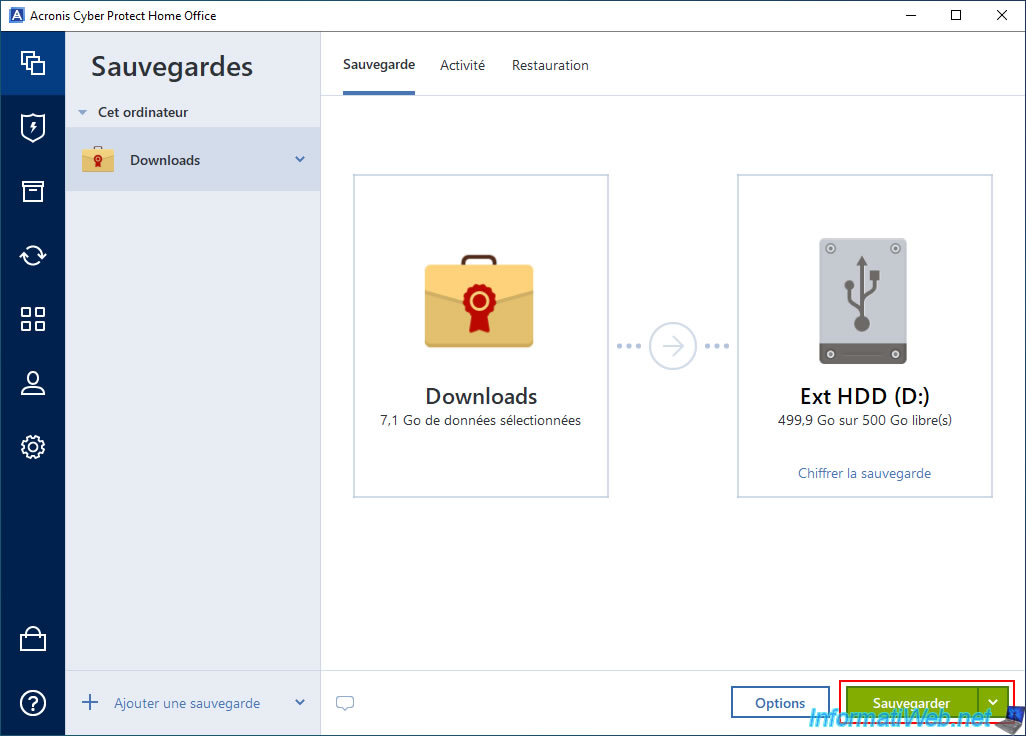
Please wait while the folder is backed up.
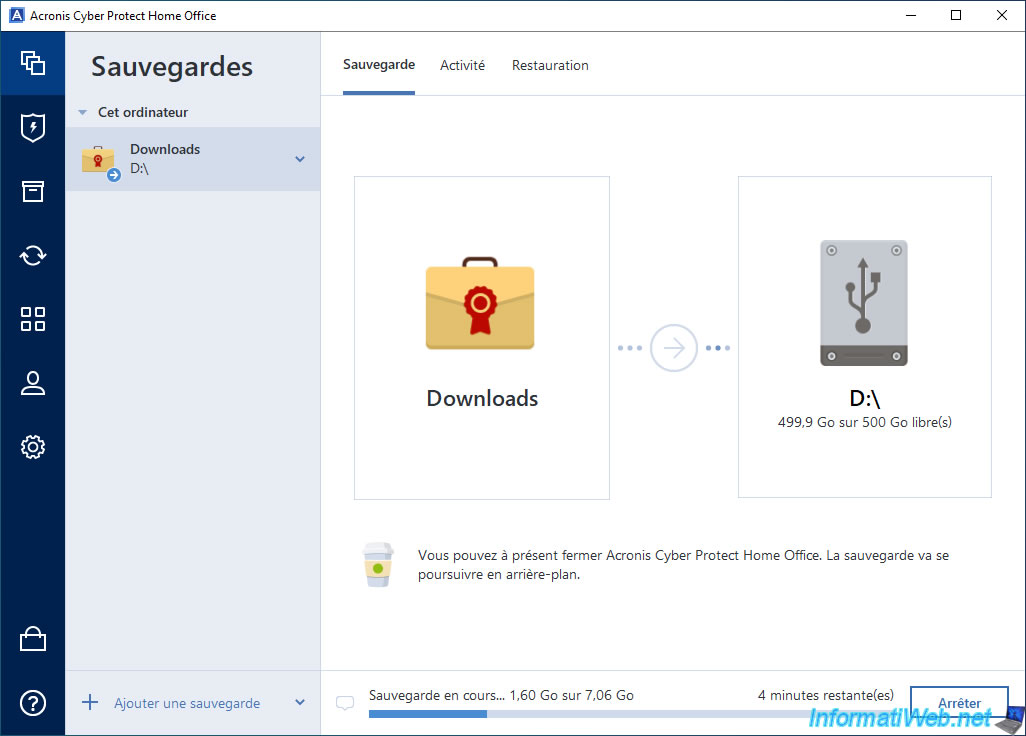
Once the backup is complete, you will see that the last backup was done today.
In addition, you will see the message "Compliant Certification in Progress" appear for a while.
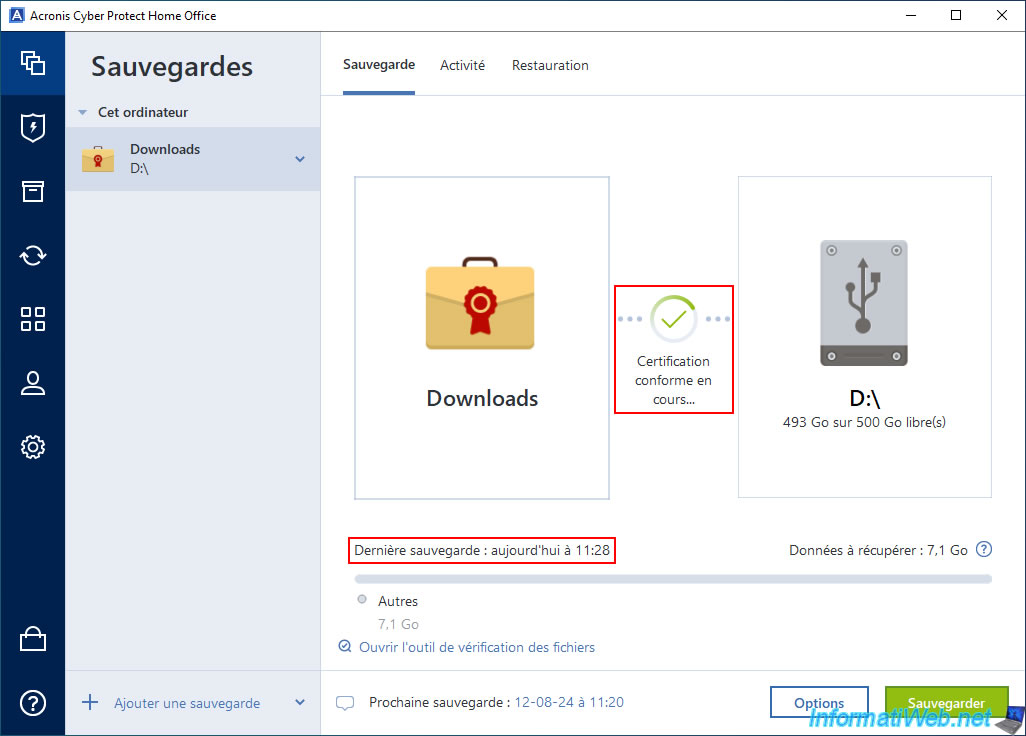
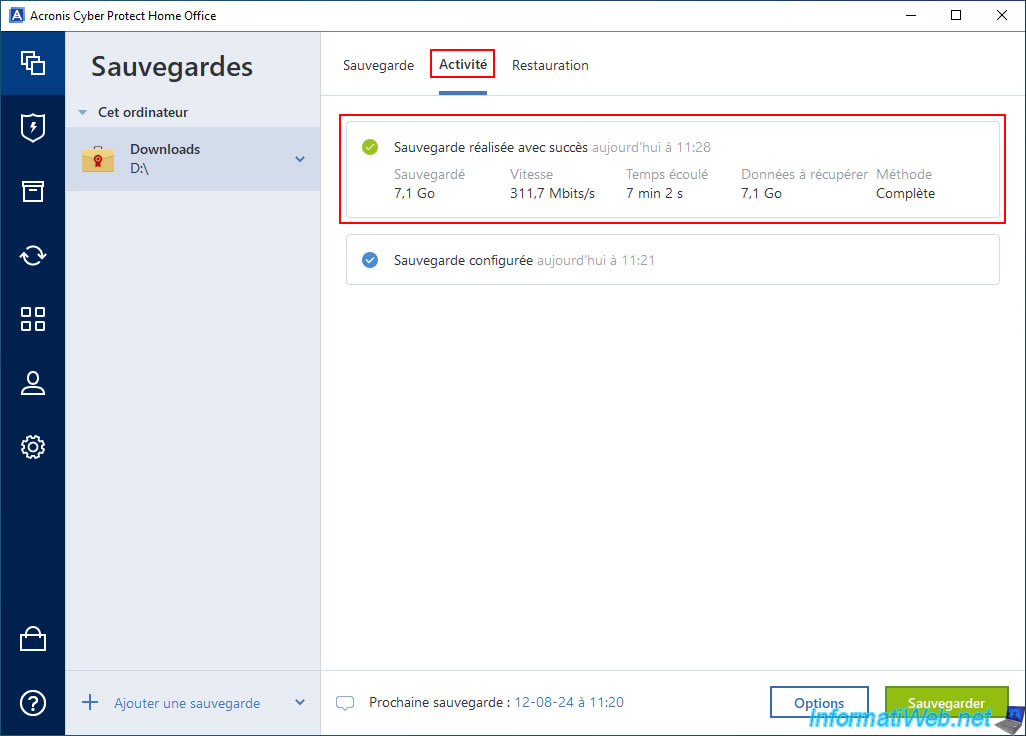
If you now go to the "Activity" tab, you will see that the backup is complete.
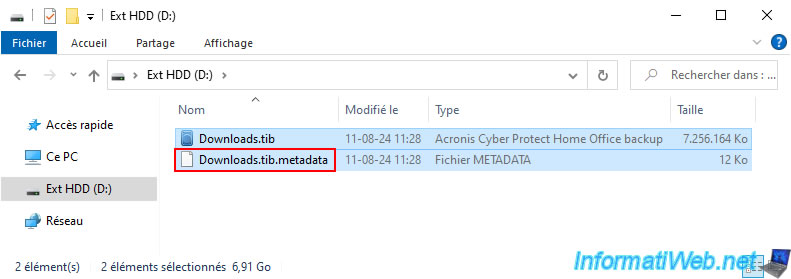
On your external hard drive, you will see that an additional file with the extension ".tib.metadata" has also been created alongside your usual ".tib" backup file.
3. Certification in progress
If you leave the Acronis Cyber Protect Home Office (True Image) window open, you will see that the message "Certification in progress" will remain displayed for a very long time (after more than 5 hours, the message was still displayed).
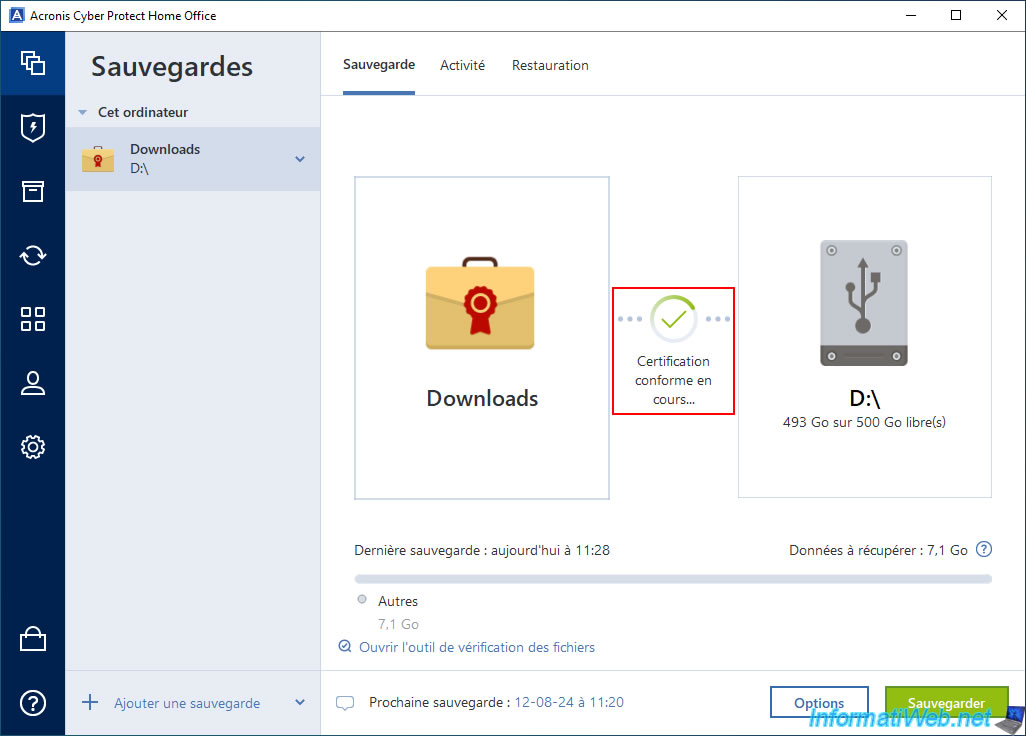
To proceed to the next step, close the Acronis Cyber Protect Home Office (True Image) window and relaunch this program.
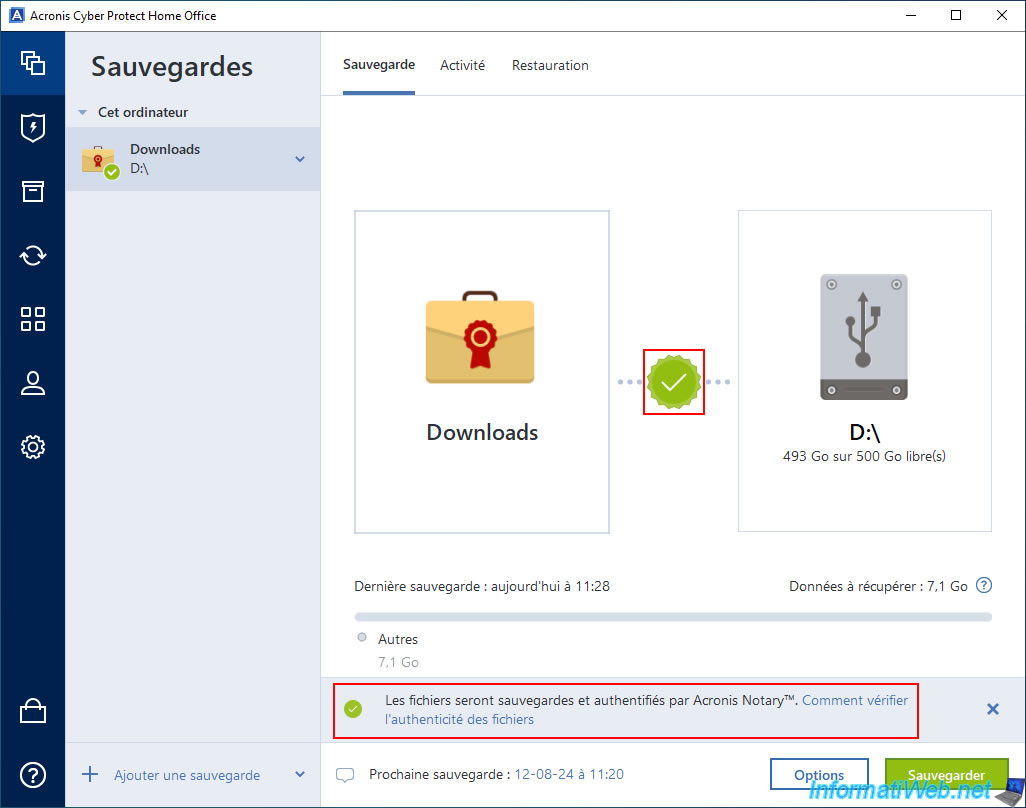
Now a green icon with a "V" appears. This means that the files in your backup are compliant.
At the bottom, you will also see a message telling you that the files will be authenticated by Acronis Notary.
The link indicated by Acronis Cyber Protect Home Office (True Image) will redirect you to the page "Verifying file authenticity - Acronis Cyber Protect Home Office (True Image) - User Guide for Windows - Acronis".
Plain Text
Files will be backed up and authenticated by Acronis Notary. How to verify file authenticity.
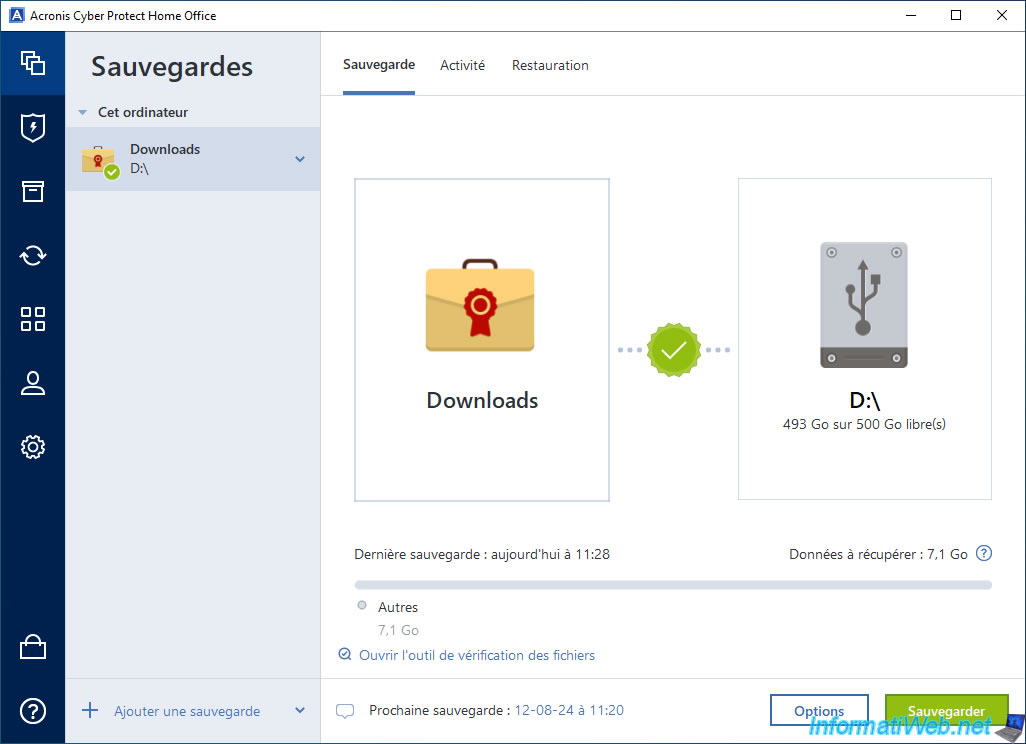
If you hide this message by clicking on the cross on its right, you will see a link "Open file verification tool" appear.
This link will allow you to access the official site "Notary Console - Acronis".
Share this tutorial
To see also
-

Backup 9/1/2025
Acronis True Image - Backing up your smartphone to your PC
-

Backup 7/7/2025
Acronis True Image - Backup files or folders
-
Backup 12/22/2025
Acronis True Image - Clone a disk (manual mode)
-
Backup 7/31/2025
Acronis True Image - Create backups (single version)

You must be logged in to post a comment